Table of Contents
Sometimes your system can generate an error indicating all types of spyware and adware, including keylogger trojans. There can be many reasons for this error.
Approved
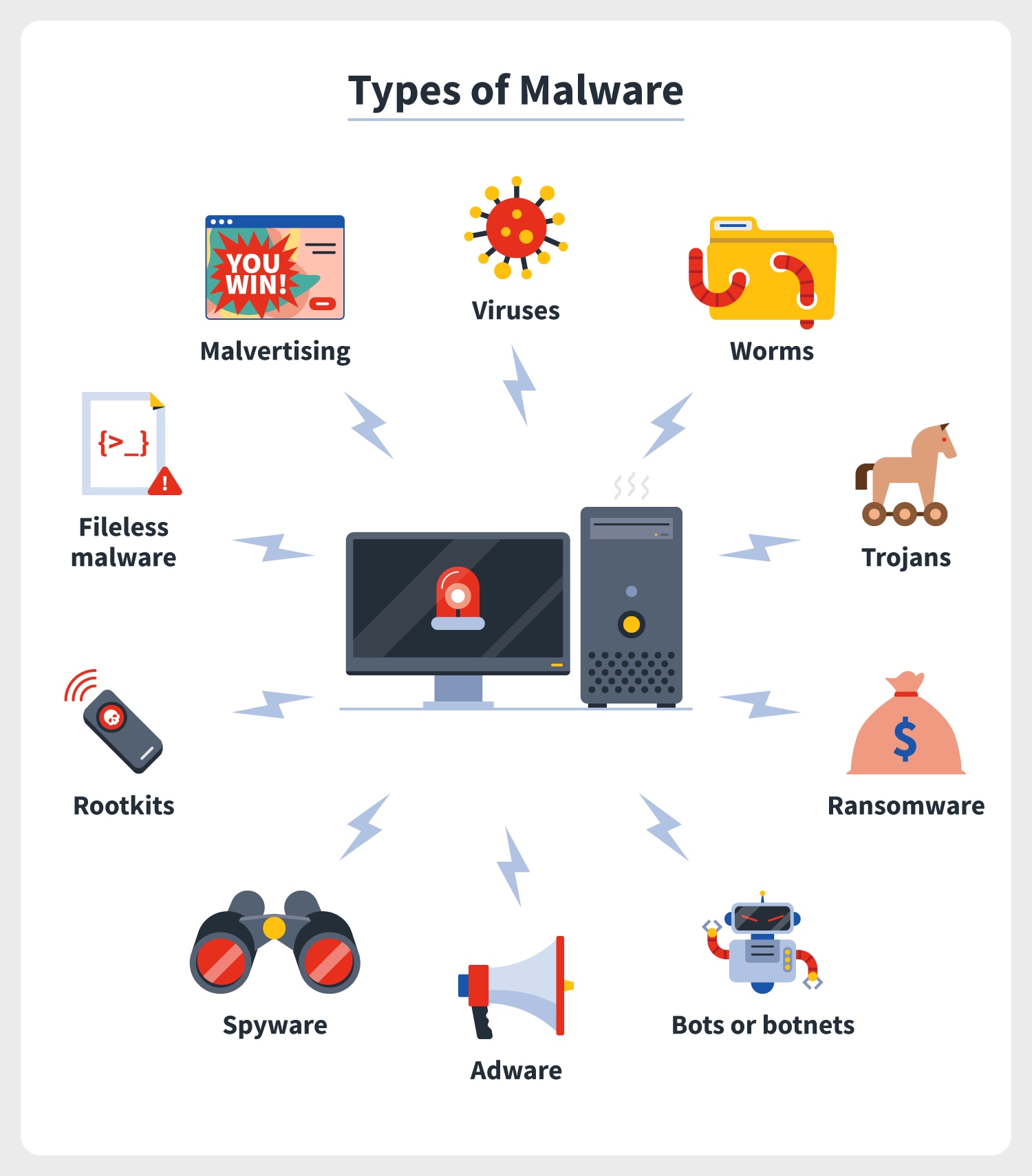
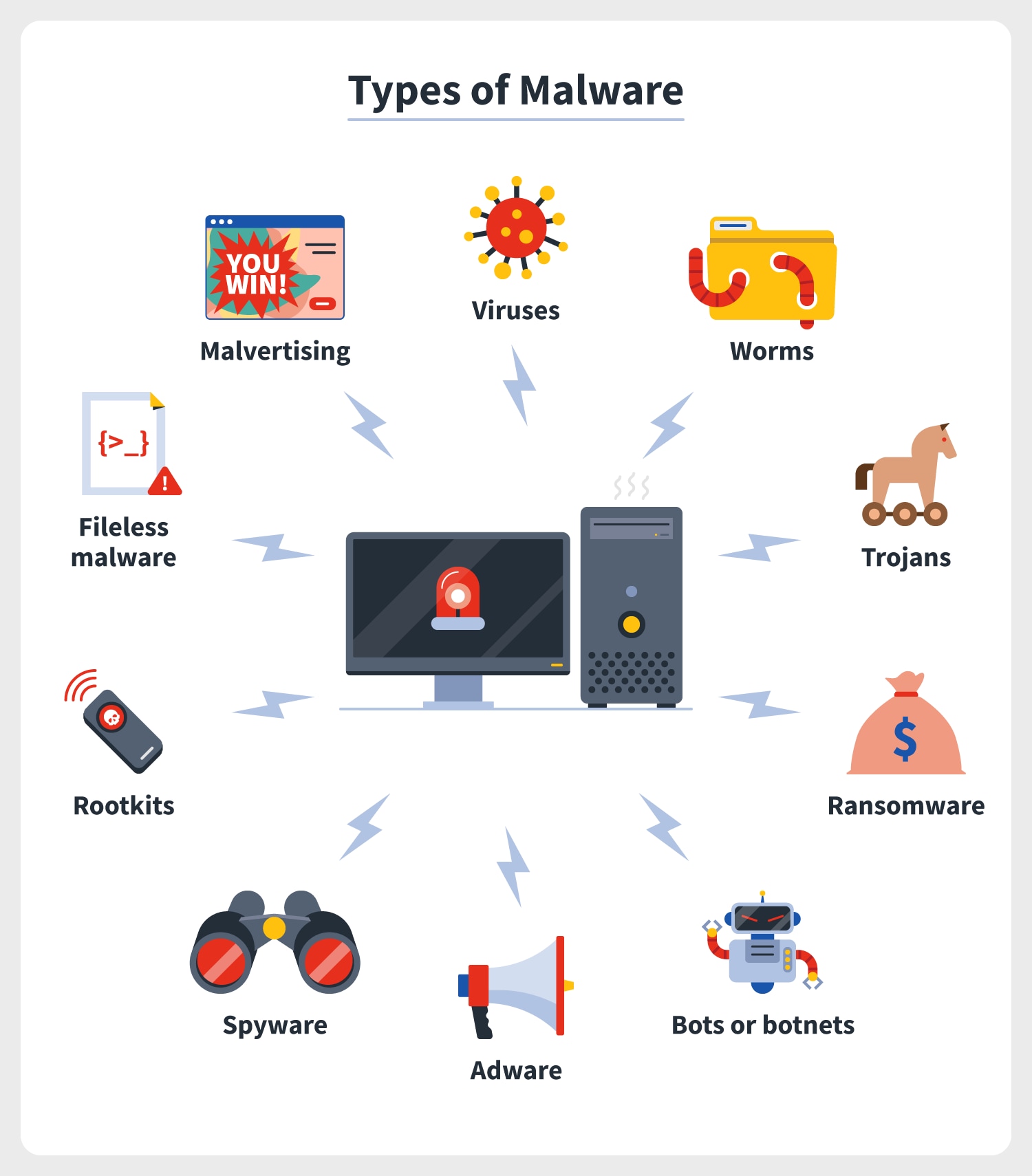
Nearly all common types of malware include viruses, worms, Trojans, ransomware, bots, as well as botnets, adware, spyware, rootkits, fileless or spyware, and malicious ads.
The most common types of malware are viruses, keyloggers, red wigglers, Trojans, ransomware/ crypto-malware, bots / botnets with common sense, bombs, adware and spyware, and rootkits. You can mitigate or prevent spyware and adware attacks by developing security policies, providing security training using application-based multi-factor authentication, installing filters to protect against malware and malware, spam, modifying standard operating policies, system voting capabilities, and performing routine vulnerability assessments.
With regard to this note, it is important that no system is 100% free of security vulnerabilities or “tamper-proof”. If a single attacker has the time, location, and manpower to launch an attack, chances are good that he will get in your way.
Article Navigation
What Is Malware?
Malicious software, destructive software, is a software system written with the intention of harming data, inventions or people.
Systems infected with spyware or spyware show symptoms such as slowdowns, sending emails without user intervention, accidentally restarting or starting unknown processes.
There were various types of spyware such as browser hijacker, adware, Papan-Ketik recorders and many more. Each type associated with such malware has its own unique way of working.
Malware use of To-Meaning vulnerabilities continues to grow year after year, reaching a record high of 812.67 million infected trackers in 2018.
Learn More: How to Develop and Implement a Network Security Plan
How Does Malware Infect A Computer Or Network?
There are a number of techniques that attackers use to inject malware directly onto a network or system, including emotional engineering and exploitation of vulnerabilities.
Social Technologies
Malware is likely to spread widely through vishing, phishing, and smishing, which are all types of social engineering attacks.
Malicious software.Cryptocurrency mining.Mobile malware.Botnet.Reseller information.Trojans.Other malware.Protection.
KoIn short, celebrities are trying to obtain confidential information and trick people into clicking links, downloading available attachments, or providing access through that phone.
If successful, the malicious payload will undoubtedly be delivered, and you can assume that you yourself may be harmed.
Exploiting Security Vulnerabilities
One of the simplest techniques an attacker can use to infiltrate a system or network is to deliver almost any number of known corporate exploits, such as Kerberoasting.
This is called trial and error, but a higher technical education is built into the whole process.
You can devise the best strategies, scan the network weekly and therefore patch systems daily, but you are probably never 100% free of vulnerabilities.
If your custom system fails stress testing, you cannot decide if store security measures are appropriate.
Test Penetration testing is used for guided testing not only of discovered vulnerabilities, but also for evaluating the implementation in terms of security controls and tools.
Common Types Of Malware
Approved
The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today!

Malware comes in many forms, but remember that the following types are the most common:
- Virus
- Keylogger
- in
- Trojan horse
- Cryptocurrency ransomware
- Logic / Bombs
- Bots / Botnets
- Adware and Spyware
- Rootkits
1. Virus Virus
a is the most common type of malware attack. For a real virus to infect a system, the concept requires the user to click on it, or perhaps copy it to important media or host.
Most viruses reproduce without the user’s knowledge. These viruses can be transmitted from one to another via email, instant messaging, website downloads, removable media (USB), and Internet connections.
Some file types are more susceptible to virus infection – .doc / docx, .exe, .html, .xls / .xlsx, .zip. Viruses usually remain dormant until they spread across a network or a number of devices, or before they deliver their payload.
2. Keylogger
Keylogging or keystroke logging records the keystrokes of the real user and sends the data to the attacker.
While there are times when employers use keyloggers to track employee actions, in most cases they are encouraged to steal passwords or sensitive data.
Keyloggers can be a physical cable that is discreetly connected to a device, such as a specific keyboard, or installed by a Trojan horse.
3. Towards
Like a virus, an earthworm can reproduce and distribute large copies, and its segments indicate network connections, attachments, emails, and instant messages.
However, unlike viruses, the worm does not actually need a host program to replicate and propagate.
Worms are widely used against mail servers, servers, web servers Oers and database servers.
Once damaged, worms quickly spread across the Internet and computer networks.
4. Trojans
Malicious spyware also tries to intercept users’ passwords and personal information by running in the background on the system. Little. Trojan Horse: The Trojan Horse was also a type of malware that uses fake and bogus names in the belief that it misleads users about their true intentions and fulfills them.
Trojans are malicious programs that are considered legal.
A Trojan horse hides on your computer until it is called.
If Trojans are activated, attackers can most likely spy on you, steal your sensitive data, and also gain access to the corresponding system through the back door.
Trojans are usually downloaded via email URL attachments, downloads and instant messages.
Social procedural engineering is commonly used to force users to download and run Trojans on their systems. Unlike microbes and computer worms, Trojans cannot reproduce themselves.
5. Ransomware / Ransomware
Ransomware is almost certainly a type of malware designed to exclude users from their plan or deny access to data until the ransom is paid.
Crypto-malwareAxis software is a great type of ransomware that encrypts end-user files and requires payment for a very long time, often in your own digital currency such as bitcoin.
6. Logic Bombs
Boolean bombs are a type of adware that only activates when they appear, for example, on a specified date / time or on the 25th login.
Viruses and worms often have logic bombs that must be delivered with predetermined effort (malicious code) or when some other condition is welcomed.
The software to fix your PC is just a click away - download it now.