Table of Contents
Over the past few days, some users have reported spyware on mobile phones.
Approved
Some people argue that it is possible to extract a person from the target phone without installation, simply by spying on the phone with each phone number. But this is completely impossible. Cell phone spyware is used as a bug to write target device environment and read it later.
Spyware or stalkerware refers to software – applications, programs, and additionally – devices that allow another man or woman (for example, an attacker) to invisiblymonitor, combined with the recording of information about your training over the phone. The term “stalkerware” is a much newer term that attracts attention, so you might see an intrusive, aggressive and dangerous waste of these tools.
Phone spyware is special and extremely dangerous for survivors because it can track many things you do on your smartphone, including the photos and videos you have purchased, websites. Internet that you visit, text messages that you can send and receive. , recordings of conversations and your location. Spyware installed on rooted (Android) or jailbroken (iPhone) devices can allow an employee to turn on their webcam or microphone, take screenshots, view activity in last-party apps (such as Snapchat, WhatsApp), and intercept , forward or call. background. (A rooted phone or even a jailbroken phone removes the protection that the operating system and phone manufacturer has added to the phone.The phone is unlocked without your knowledge, which may give a hint about the software. Spyware may have been installed.)
Nearly all spyware for phones requires that this particular person have physical access to each of our device settings. Remember, once installed, it will run in stealth mode without any notification or activity identification, and is often too difficult to detect or remove from your device.
But in 2015, the AVG Mobile Security team discovered a new type of malware that could challenge this prejudice. This is a terrific type of spyware known as Android / PowerOffHijack that kills the entire process to make your phone look like it’s turned off even if it’s still running.
How do I know if my devices have spyware?
Finding spyware on your home phone can be difficult. Symptoms may include fast battery drain, device fatigue, and / or data usage spikes. However, the most common indication that your activity is being monitored may well be the behavior of the offender in question. For example, they may be too confident about what you are doing on their smartphone without further explanation. Trust your information and look for patterns. If the attacker knows too much about the attackerWhether your phone is active or knows the circumstances that you only created on your phone, there may be spyware on your device. A new qualified technician may need to check some equipment to be sure.
Safety first. Before taking any steps to find or even remove spyware, it is important to consider its security and the ability to obtain evidence. Many attackers use spyware to control and manage survivors. Some offenders may intensify their acts of harassment and abuse if they suspect that their heir is repressing them. Before removing spyware, think about real security and how to protect yourself, and talk to a real lawyer about security planning. If you need a lawyer, contact the National Domestic Violence Hotline directly.
Whether you are using Android or this iPhone, anyone can install spyware on your device that secretly reports real activity. Your kids can even follow the movement of your cell phone without even touching it.
Collect evidence. Law enforcement or this computer forensics expert can help you if you need to preserve your doc Obligations required for a specific criminal investigation or civil behavior. Your forensic tools cannot determine with certainty if your device has spyware. Learn more about Evidence Spyware.
Spyware removal. In most cases, resetting the installation will remove the spyware. Be careful when reinstalling apps or versions from a backup, app, or play store, as this could accidentally download the spy app again. Manually add the application software or the software you need the most to the connection. You can also confirm the step of creating a new iCloud or Google account for your device and use that description to download apps. If you want to do a reset, then the advantage is that the phone is not connected to the backup reinstallation of apps, contacts, photos, etc. If this happens, it is very likely that the adware will be reinstalled as well.
Use devices that are not monitored. If you think your chitator is spyware, keep in mind that most of your processes, including conversations, could be exposed to an attacker along the way. If possible, get a safer computer or an Apple iPhone 4 — a computer that a person doesn’t have skilled physical or remote access to, such as a computer, a larger public library, a community center, or a real friend’s phone — if you need help or information.
Update your accounts. Since spyware would give men or women access to your credentials, it would be a good idea to reset your passwords on an amazing device instead of accessing various accounts over the phone, as you may fear deleting them from the website. Also consider changing passwords for sensitive accounts such as online banking, major social media, etc. Learn more about security passwords.
Consider accessibility. Be skeptical if someone wants to update or possibly fix something on your phone, and trustthose of their intuition when someone does not trust their intentions. Beware of gifts in the form of a new cell phone or tablet from the abuser, which should be you or your children.
Lock your precious phone. Since most spyware requires a lot of manual work to gain access to your phone, lock that phone with a password (and do not divulge it) to minimize the risk of someone installing the spyware. Many devices allow you to choose between number, pattern, fingerprint, and possibly other security features. Additional tips to keep your phone safe. Class = “”> Usage
Use the security features of your work phone. Most Android phones have a setting that allows unknown installation alternativ. Disabling this option minimizes the likelihood that apps will be hosted outside of someone’s Google Play Store on someone else’s phone. Another feature related to Android phones is the full inclusion of Play google Protect, which will look for apps that contain malware and Trojans that can protect your phone from most spyware anywhere. Also, make sure your phone is always running the latest operating system updates, which often contain basic security fixes.
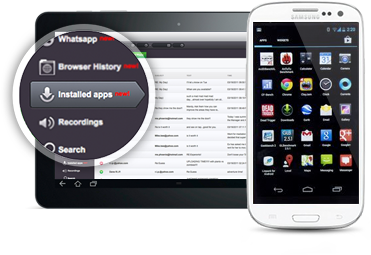
Do not root (for Android phones) or jailbreak the iPhone) (for the respective phone. Most of the additional aggressive spyware features do not work unexpectedly as the phone is rooted and also jailbroken. Can only be installed if if it’s jailbroken. A rooted or jailbroken phone becomes more susceptible to viruses and adware, and makes it easier to install spyware.
Approved
The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today!

There are a number of other methods you can use to access informationactions on your phone to install spyware. If an abusive young person has physical access to a mobile phone, they may not need to install spyware, which is primarily intended for online computer support.
Most applications and simple accounts on phones are automatically accessible from another device if the attacker knows the username or Internet mail and password. Phones can also be monitored via iCloud to monitor iPhones and Google Android phones. Enhance the security of personal accounts by making sure no one else knows your username and password.
Sometimes a cruel person knows a lot about their limbs and befriends them. Look for trends in what the person is familiar with and where that information comes from to narrow down your options. A lawyer can help people understand what might happen and plan next steps.
The software to fix your PC is just a click away - download it now.