Table of Contents
This guide is intended to help you when you receive an event Viewer Connection Event ID error.
Approved
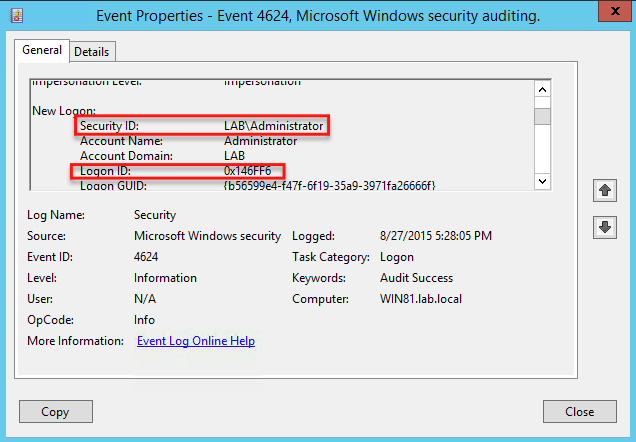
Event ID 4624 (displayed in Windows Event Viewer) documents every valid connection attempt to any local computer. This event is won on the machine that was evaluated, that is, on the H. on which the connection session was created.
Event ID 4624 (displayed in the Windows Event Viewer) is logged each time a successful attempt is made to access the local computer. This event generates on a home PC accessed by different search terms where the logon session should have been created.
Approved
The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today!

Determine whether to check each instance associated with user login to eventually log out of the device.
Account login events are generated on game controllers and domain local account actions for devices to assign a local account. If the “As a logon account” and “Audit logon” policy categories are enabled, logons that use a domain account generate logon or logoff events on a work station or server can generate an account event connection associated with a domain controller. In addition, a good login to the system on private withserver or why workstations use a domain account generate a logon event on the sector controller, since scripts and logon policies are retrieved when the user logs on. For more information on account events, see Verifying Merchant Account Login Events.
When you set this security setting, you can specify whether the type will have audit success events, consider audit failures, or not audit. An audit error created an audit entry because the login attempt failed.
To set me to ‘No monitoring’, I would say that in the Security Settings Properties dialog box, I have these ‘Set Policy Scope Settings’ checked, and usually both ‘Pass’ and ‘Fail’ are unchecked.
p>
For more information about advanced security policy settings for event logon, see
Configure This Configuration Audit Option
Connection ID: The last semi-unique number (unique between restarts) that corresponds to the connection session just initiated. All events subsequently logged during this login session report the same login ID up to and including logout 4647 or 4634.
Show event connections for specific milestones 1. Go to “Start” ➔ Type “View and Events” press “Enter” to open this special “Event Viewer” window. Step a. In the left navigation pane, under Event Viewer, open and Security, save Windows Logs.
set the security option hereSpecifically by opening the large Computer Policy ConfigurationWindows SettingsSecurity SettingsLocal folder under PoliciesAudit Policy.
| Effectively Custom Events | Description |
|---|---|
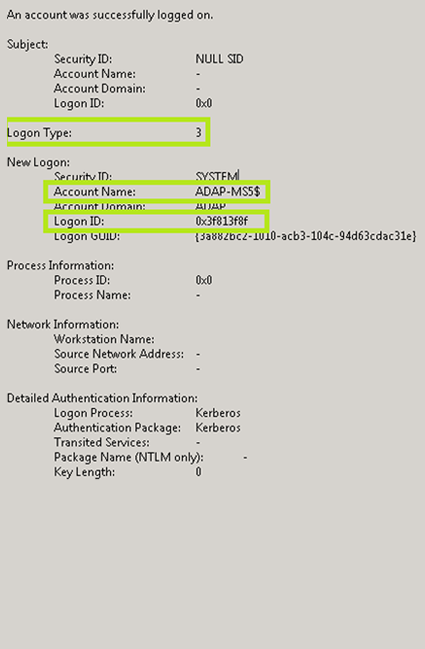
| 4624 | A is connected to a computer. Connection Type See “Connection Types” below. |
| 4625 | Connection failed. An attempt was made to login with an unknown username and a known username with a malicious password. |
| 4634 | User logged out for. |
| 4647 | The user has initiated the disconnect user process person. |
| 4648 | user successfully logged on to a computer with explicit knowledge when it was already registered for another user. disabled by user |
| 4779 | a fatal session server without logging out. |
If a collection is logged (legacy event 4624 Windows ID 528), the connection type is also simply reported to the event in the firewood. The following table describes each connection type.
Connect to this readabilitydatatable=”1″>
Request Name
Description
Have you ever wanted to keep track of who logs into your computer and when? In professional editions outside of Windows, you can turn on logon audit times so that Windows knows which company user logs in and when.
Open Event Viewer in Active Directory and go to Windows Logs> Security. The area in which the center lists all the events configured for monitoring. You should look at the registered instances to check for unsuccessful connection attempts.
Configuring connection audit events monitors both localized and network connections. Every login timeCalls the user account that impregnated and the time the event occurred on the network. you can also define when users log out. USAGE:
Relevant Display As Previous Credentials On Current Windows Logon Screen
Note. The Login Verifier only works on Windows Professional, so you can’t use this idea if you have a home copy. It should work on Windows 8, Windows, and Windows 10. In this type of article, we’ll cover 10 windows. The screens may be slightly different in other versions, but the process is basically the same.
Enable aria-level=”2″ login verification
To enable login verification, use the Local Group Policy Editor. It’s quite a powerful tool, and even if you’ve never used it before, it will take some time to get to know its full potential. If you’re on a corporate network, do everyone a favor and check with their family administrator first. If your computing work device is part of a domain, it’s all too likelyClearly, it is part of a group domain, a policy that can override local group policy. Open
To run the Group Policy Editor locally, type “gpedit sie.msc” and select the upload result.
Step 1. Go to Start ➔ Type Event Viewer and press Enter to open each of our Event Viewer windows.Step 2. Left In the first navigation pane in Event Viewer, open Security Logs via Windows Logs.Step 3. You will be looking for the following tournament IDs for the purposes listed below. Event identifier.
In the Local Group Policy Editor, in the left pane, go directly to Local Computer Policy > Computer Configuration > Windows Settings > Security Options > Local > Policy Audit Policy. On the panel, double-click the Audit connection event rights option.
Right-click custom views in Event Viewer and select New Custom View.In the Event Logs section to the right of By Log, select Windows Security Log.Enter 4624 in the
Right-click the appropriate Start button and select Control Panel > System and Security, double-click Administrative ToolsRirovanie”. Double-click Event Viewer.
Open most of the desktop event viewer by directly “View by typing events” in the Cortana/search box.On the left, select Windows, Logs, Dish area.Select Windows Security Logs.You should now see a scrolling list of all security events on your PC.
When the session ends, tournament 4634 connections are generated. However, this should not be confused with action 4647, which initiates a logout of all users (i.e., a particular account definitely uses the logout feature). Here it is easy to see that the session no longer exists because it has ended.