Table of Contents
Approved
If you have Gentoo-protected kernel sources on your system, hopefully this guide will help. The sys-kernel / hardened-sources kernel was based on the slick Linux kernel and was intended for users who ran Gentoo on server components. He has previously provided fixes for these various Gentoo Hardened subprojects (e.g. SELinux support, not to mention grsecurity), as well as stability and security improvements.
The sys-kernel/hardened-sources kernel was based on the official Linux kernel and was intended for people running Gentoo on server systems. He provided fixes for various types of Gentoo Hardened subprojects (due to SELinux and grsecurity support, for example), as well as stability and security improvements.
File:Virtual memory.svg
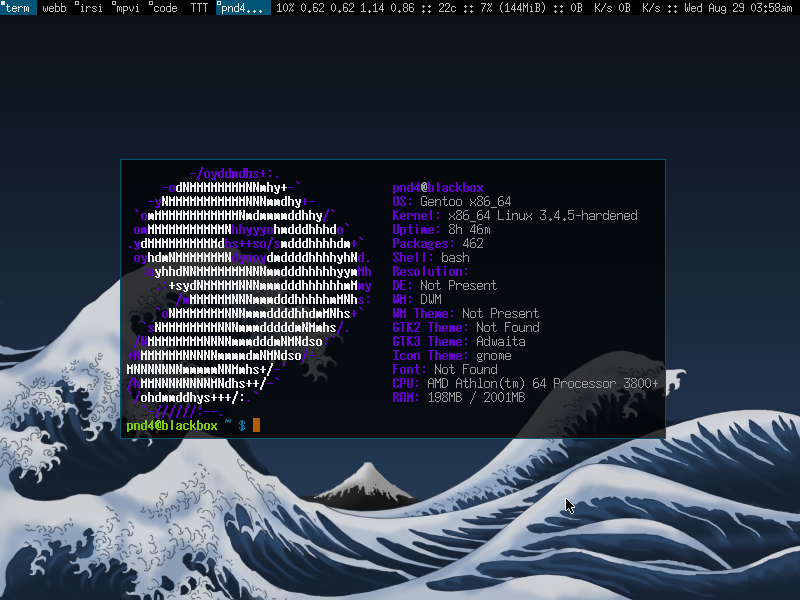
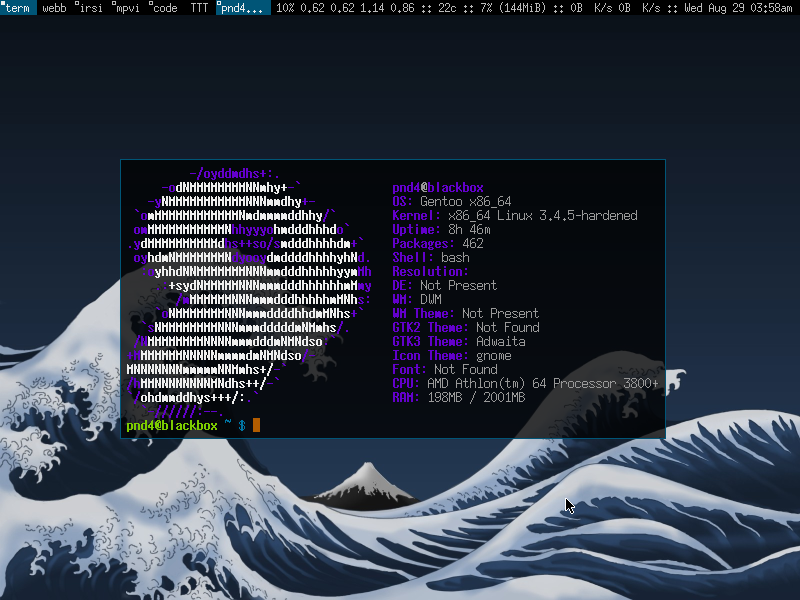
Gentoo Hardened is a kind of Gentoo project that offers several additional security services in addition to some well-known Gentoo Linux installations. Increasing the security of a system means that you have additional measures to counter attacks and some other risks, and this is usually a general set of actions that you perform on the system.
The solution assumes it has multiple contiguous addresses; but in the world, the parts that are currently in use can be scattered across RAM, and usually the inactive parts are stored in every file on disk.
In computers, virtual memory is a memory management technique designed for multitasking kernels. One such method virtualizes a set of computer architecture hardware storage devices (such as RAM modules and hard drives) where the memory has a program to be fundamentally designed:
- there is only one deviceA real storage device, and this “virtual” device acts as a RAM module.
- By default, the program has exclusive access to this virtual RAM module as a point of view of the contiguous working memory space (address space).
- Make better use of hardware memory than without virtual system memory.
- Simplify programming this custom sharding application by doing the following:
- Hide.On
- Delegation of load to the kernel to manage the memory hierarchy; the program does not need to explicitly handle overlays either.
- Avoid moving programs or code to obtain relative memory.
Gentoo Hardened is a Gentoo task that offers several additional security agencies in addition to the well-known Gentoo Linux installation. Technique hardening means that you are taking similar countermeasures against attacks and other risks, so it is usually a combination of actions that you take to accomplish a given function.
Memory virtualization is often a generalization of the concept of virtual memory.
Virtual memory is an integral part of computer architecture. Every implementation (with the exception of [doubtful – discuss] emulators as well as virtual machines) requires a hardware backup, usually in the form of an actual memory management unit, plugged in.military in the main CPU. As a result, older operating systems (such as 1980s DOS[1] and those on my 1960s mainframes) generally don’t have virtual memory features, though notable exceptions are the B5000, Atlas, IBM System. /360 model sixty-seven, the IBM System/370 mainframe systems of the early 1970s, and the Apple Lisa project of the circa 1980s.
grsecurity is almost certainly a series of Linux-specific security patches. While grsecurity uses different protection strategies to sometimes even stop unknown problems, always (0 days) – additional checks, random design and style (more than a regular kernel), write protection of memory.
Embedded systems and additional specialty computer systems that require extremely fast and/or very stable response times may choose not to use web storage due to reduced determinism; Electronic storage systems generate unpredictable interrupts that can cause unwanted jitter during I/O operations. Indeed, the cost of embedded components is often kept low when such operations are implemented on demand (a technique called bit burst) and compared to dedicated hardware. All chassis-embedded systems typically have low power consumption for multi-tasking functions or complex storage hierarchies.and I.
History
In the 1940s and 1950s, any major program to start developing virtual memory had to include common sense to manage most of the memory at two levels (primary and secondary); One such capture technique is layering. Therefore, the main reason for introducing virtual memory was not only to significantly increase the amount of memory, but also to make such a proxy as convenient as possible for web developers.[2]

To enable multitasking and/or multitasking, many early systems suffered from the ability to share multiple programs from memory even without virtual memory mapping; For example, early PDP-10 packages provided memory browsing through so-called base and/or boundary registers.
/ var / db / repos / gentoo / profiles is any directory containing global profiles. The idea is controlled by the developers, whose main ebuild repository (gentoo.git). One of them must be selected as the system profile. To bypass these settings, use the files in the / etc / portage / profil / directory.
Paging was first developed with the participation of the University of Manchester as a reliable and inexpensive way to expand the memory of an Atlas computer by transparently adding 16,000 words of main memory, which is the most important, with an additional 1,000 words of secondary drumdisk. Although the first atlas was originally commissioned in 1962, working prototypes related to pagination were not developed until 1959.[2](p2)[3 ]< /sup>[4] In addition, in 1959, Burroughs independently produced the first commercial mass storage computer, practically the B5000,[5][6 ] . really used segmentation as pagination.
Like many other technologies in the history of computing, virtual memory storage was not readily accepted. For earlier adoption to traditional walking systems, many models, experiences and lessons had to be developed to overcome many problems. Dynamic address translation required expensive specialized hardware that was probably difficult to build. In addition, early implementations slowed down memory access [2] even more. There were also concerns that completely new system-wide algorithms using secondary memory would be less efficient than previous application-specific algorithms.
The term kernel hardening refers to a strategy most commonly associated with the use of specific parameters in kernel configuration that can restrict or prevent certain types of cyber attacks. You can use these types of options to create a better scoring system.
In 1969, the main debate was aboutCommercial computers ran out of memory before then.[2] An IBM research team led by David Sayre showed that their memory overlay system was always more capable. than the best manual systems.
The Norwegian NORD-1 may have been the first minicomputer with primary memory. In the 1970s, other minicomputers implemented online storage, especially VAX models using VMS.
Virtual memory was typically introduced in x86 architecture with protected mode on all Intel 80286 processors; However, rest assured that this is a shard replacement technique, discovered as a way to scale poorly over wider shard ranges. The Intel 80386 introduced support for paging within an existing segmentation gap, and the page fault exception can be linked to other exceptions that do not cause a double fault. The 80386 did not have a translation search buffer (TLB), which made load phase descriptors expensive and forced operations developers to rely solely on paging rather than a combination of paging and segmentation.
Pageablevirtual Memory
Approved
The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today!

Almost all virtual memory implementations paginate the application product’s Internet address space; a is the right side of the block of relevant virtual memory information. Pages are typically at least six KiB (4 × 1024 bytes) in size, in addition to systems with large virtual address types or large amounts of real memory typically using large network page sizes.
The software to fix your PC is just a click away - download it now.The term “kernel hardening” refers to the strategy of using certain kernel configuration settings to limit or prevent certain types of cyber effects. You can use these options to create more securenoah system. To remove a feature, use menuconfig to disable the feature.
A profile is a set of configuration files stored nearby in the /var/db/repos/gentoo/profiles subdirectory, which just describes things since ebuilds, which are considered packages, are standard USE flags, and the architecture in the diagram is Run.
grsecurity is a set of Linux kernel fixes designed to improve your security. While grsecurity uses various protection strategies to stop even new (0-day) errors – similar checks, random placement (above and after the normal kernel), write access memory protection.