Table of Contents
Approved
If you don’t have a password hash loaded on your system, hopefully this guide should help. It says “No password hashes loaded”, “No code hashes loaded (see FAQ)”, in addition to “No password hashes to saturate 15 (see FAQ)”. A: Your boot password from a Unix-like system may be hidden. You need to have both /etc/passwd and a shadow history (usually /etc/shadow or /etc/master.
John the Ripper uses the dictionary method preferred by attackers as the cheapest way to crack a password. It samples text strings from a kind of list of words, using commonly used dictionary words or common passwords.
Forgive the newbie for being insecure, but everyone has to start somewhere, right?
After reading this excellent eBook, I’m trying to get to know John. I’ve gone through the FAQ and this guide, but I’m stuck.

I generated a SHA256 password hash. It’s simple. The password can be a “password” that has been salted and hashed only once. Now I want to use a hack tool to make sure you do it.
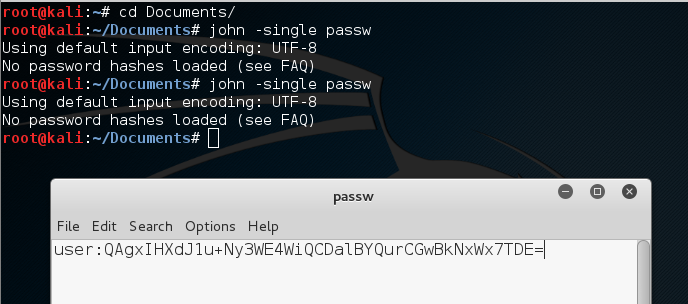
I saved it in an IN file in what I think should be the correct format (see screenshot below).
When I run the following command, I get a message”Security password hash not loaded”
John the Ripper is a truly free and open source password cracking tool available with a recovery security audit tool for most operating systems. It has a huge set of passwords in food format and hashes. Thanks to Crack the Password, John the Ripper now identifies all potential passwords in a hashed format.
Command: john -single passwCracked passwords are printed out on the terminal and saved in a file called $JOHN/john. The carrier (in the documentation and in this configuration file for John, “$JOHN” is moved to John’s “home directory”; the nature of the free information depends on how well you installed John). $JOHN/John.
$JohnPassword cracker John the Ripper, 1 Version 8.0Copyright (c) 1996-2013 Solar Designer onlyHomepage: http://www.openwall.com/john/Usage: Account [OPTIONS] [PASSWORD FILES]-- "single crack" mode--wordlist=FILE --stdin wordlist mode, read style from FILE or stdin-- Rules inspire word rules for word list mode--incremental[=MODE] "incremental" mode [with MODE clause]--external=MODE of external function or word filter--stdout[=LENGTH] show most recent candidate passwords [truncated when LENGTH]--restore[=NAME] Return with suspended session [name]--session=NAME Send new session to user NAME--status[=NAME] Show session reputation [name].--make-charset=FILE Encoded FILE is overwritten anyway--show Show shared passwords--test[=TIME] run tests and benchmarks for TIME seconds each--users=[-]LOGIN|UID[,..] [don't] stack these users only--groups=[-]GID[,..] put users [not] only in (these) group(s).--shells=[-]SHELL[,..] buffer only users without [off] this shell(s).--salts=[-]Load N salts, not having [out] only Nsmallest passwords--save-memory=LEVEL convince to save memory, at LEVEL 1..3--node=MIN[-MAX]/TOTAL This node numbers are outside the TOTAL number--fork=N forks N processes--format=NAME force NAME hash type: descrypt/bsdicrypt/md5crypt/ bcrypt/LM/AFS/tripcode/dummy/cryptI’m assuming you’ll test this tutorial on Kali yourself; after successful execution of the following command:
sudo unshadow /etc/passwd /etc/shadow > johninputIf you see johninput or $y$ right after logging in, it means the passwords are actually hashed with yescrypt.
kali:$y$j9T$B4i9oW2LaERt/J5/X8bbN/$zzGfRqAZim/VofZcas3MhnfSdYddB5.zRulk087PN2A:1000:1000:Kali,,,:/home/kali:/usr/bin/zshJon seems to need help recognizing most of the hash format. So try replacing the new command line with:
john --format=crypt --wordlist=/usr/share/wordlists/rockyou.txt johninputOf course, the standard Kali user account information is much faster if you just run:
john --format=crypt johninput The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today!Approved

Works with vBulletin® 4.2.2 Copyright © 2022 Solutions, vBulletin Inc. All rights reserved.
Hey guys, I’m also using Ubuntu 9.04 and downloaded John Ripper from Synaptic to see if my password looks secure…
John its Ripper is a fast Christmas password cracker primarily designed to crack Unix security (shady) passwords. Apart from encrypted Unix-like passwords, this also supports cracking Windows LM hashes and more with fixesfacilitating open buying. As mentioned earlier, the NTLM hash is very weak at encrypting passwords.
I ran the following commands
$ sudo unshadow /etc/passwd /etc/shadow > test.txt
$ sudo adam test. Then the text
it tells me
“Personal data hash not loaded”
I checked the documentation and it also says
Q: Why doesn’t John edit my password file? Gives “Password hash not loaded”.
A: Your full password may be hidden. You need to merge both /etc/passwd and the shadow file (usually /etc/shadow) and children into one file for John to work. See EXAMPLES (http://www.openwall.com/john/doc/EXAMPLES.shtml).
A: Any detailed hashes found in the document (which John recognizes as such) may have already been automatically decrypted by previous calls with John.
A: The file you are trying to run John with may not be an edit file at all.
A: Your command queue may have incorrect syntax, causing John to try to load the wrong file.
A: DesignThe name of your password file or hash types may not be supported by the version and build of John you are using. In cases where you are sure that it is a sports bag, you can search the list of resources provided on the John’s Ripper home page for a suitable replacement patch and, if unsuccessful, send a message to the air of the show (see CONTACTS (http: //www.openwall.com/john/doc/CONTACT.shtml)) including the normal password file string that John was unable to upload (please make sure the password has already been changed at the time of posting).