Table of Contents
Approved
Here are some simple methods that should help you fix your malware scanning problem. Malware is a collective term for any type of malware, regardless of how it functions, collects or distributes. A strain is a special type of spyware that copies itself by pasting its rules into other programs.
Malware is a catch-up stage for any type of malicious utility, regardless of how it works, is intended, or distributed. A virus is a special type of most malware that reproduces itself by inserting code into other programs.
Approved
The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today!

The concept is selfof the generated computer program in many cases goes back to the originally closed theories of the work of detailed automata. [1] Von John Neumann showed that the program is theoretically duplicated. This was a plausible result of the theory of predictability. Cohen Fred experimented with computer viruses and confirmed Neumann’s postulate, as well as investigated other properties of malware, such as detectability and self-obfuscation through rudimentary encryption. His 1988 dissertation on laptop viruses. [2]
Cohen’s educational advisor Leonard Adleman made a strong statement that an algorithmic determination of the overall presence of a virus is likely to be intractable in the general case. [3] Problem may occur Do not confuse change with defining after a large class of virus-free programs. This task is different in that it does not require the ability to detect all viruses.
Open Windows Personal Security Settings. Select Virus and Pending Protection> Scan Settings. Select Windows Defender Offline Scan and then select Specific Scan Now.
Adleman’s evidence as a whole is arguably the most profound discovery of virus predictability to date.day and are based on Cantor’s diagonal argument as well as the conservation problem. Ironically, Young and Jung later showed that Adleman’s work on the ideal of cryptography was to create a functional virus that is highly resistant to reverse engineering by presenting the idea behind cryptovirus. which contains and uses a fabulous public key and a randomly generated symmetric encryption initialization vector (IV) session with a key (SK).
Ransomware. Ransomware is software packages that use encryption to prevent a new target from accessing their data until the ransom is paid.Malware without a file.Spyware.Adware.Trojans.TO.Virus.Rootkits.
In a crypto-virus blackmail attack, a hybrid virus encrypts information in plain text on the victim’s computer using randomly generated IV and SK. The IV + SK are then encrypted using the virus author’s public key. In theory, the victim should negotiate with the author of the virus to get this iv + sk to decrypt the ciphertext (assuming there are only backups). The virus scan shows the public key, not the required IV and SK or understanding, but the private key needed to recover the IV and SK. This effect was the first to show that there isThe power of computer theory can be used to develop malware that is resistant to reverse engineering.
Ransomware. Ransomware is software that uses encryption to prevent a functional target from accessing their data until a certain ransom is paid.Malware without a file.Spyware.Advertising software.Trojans.TO.Virus.Rootkits.
A growing area of virus software research includes mathematical representations of the behavior of worms upon infection by purchasing models such as the Lotka-Volterra equations, which have been accurately applied in biological research on viruses. The researchers looked at various transmission scenarios for the virus, such as:
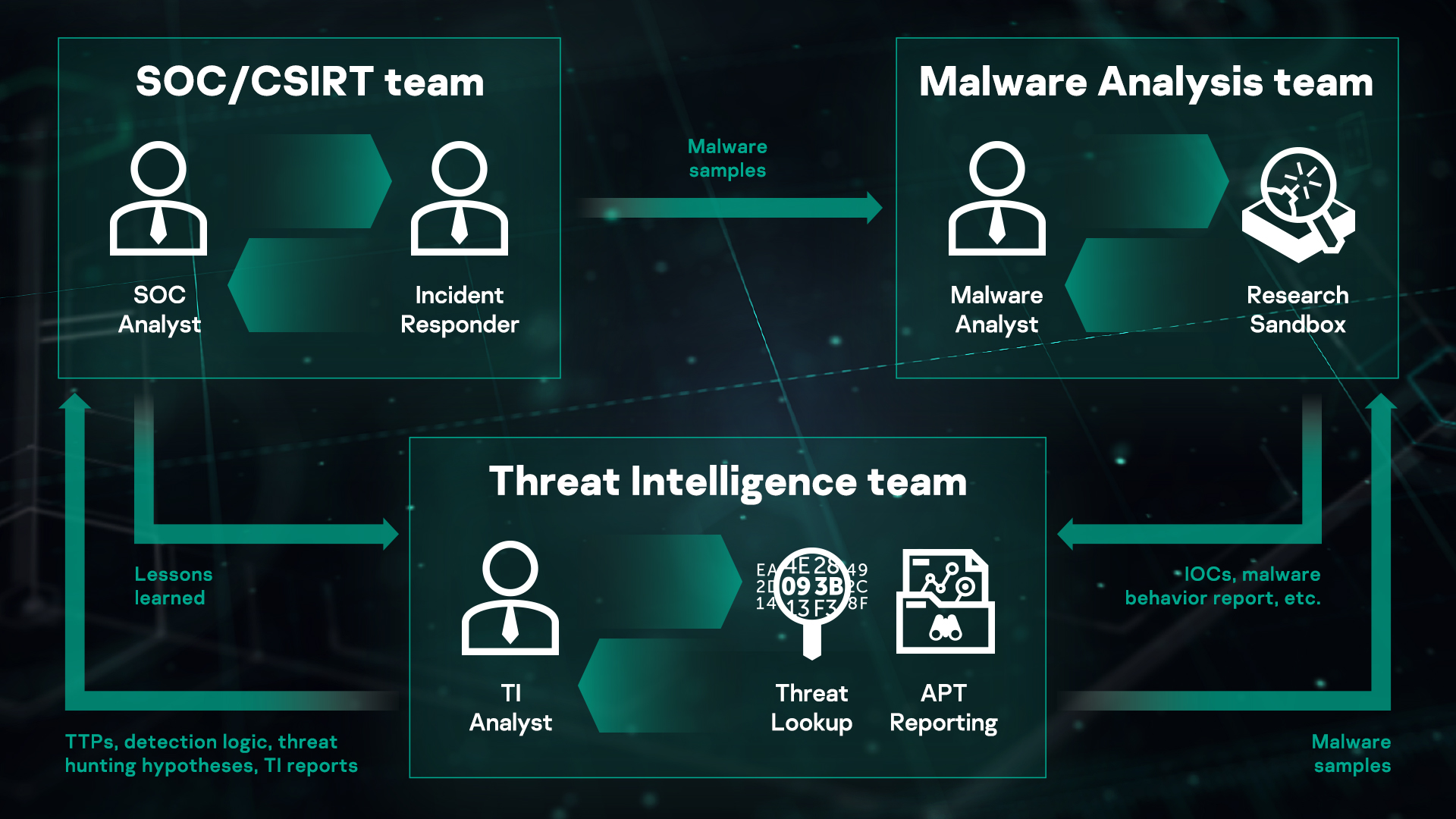
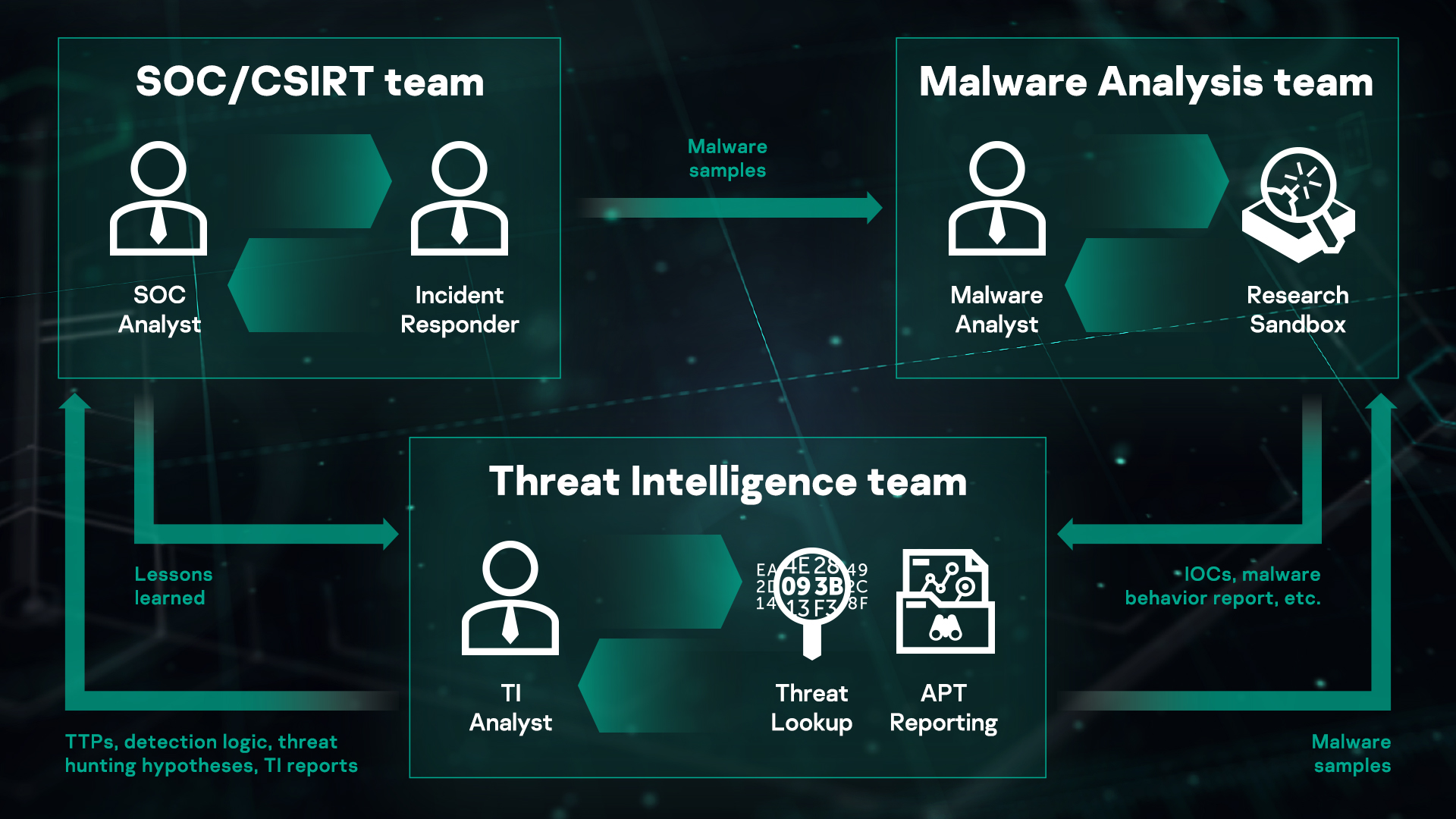
This morning we took a closer look at behavioral spyware and adware detection. Most approaches to detecting behavior undoubtedly rely on an analysis of the dependency on invocation mechanisms. The executable binary is program code built using strace or more robust pollution analysis to calculate data flow dependencies as well as system calls. The result is actually a directed graph 644a8d85ee410b6159ca2bdb5dcb9097e2c8f182 “> for nodes to be cell phone calls, system and edges to represent dependencies. For example 


You will likely also go to Settings> Update & Security> Windows Security> Open Windows Security. To run a malware scan, click Virus & threat protection. Click “Quick Scan” to scan your system for malware. Windows Security will scan and give you the results as well.
You recognize dependencies by observing whether the result matches the estimate using the new parameter value observed at runtime. Malware is detected by comparing some of the training dependency graphs and the following test suites. Fredrickson, et al. [10] describe an approach that uncovers the specifics of malware invocation system patterns. Extract meaningful behavior through conceptual analysis and jumping research. [11] Babic et al. [12] recently proposed a new classification-based approach to malware detection and grammar. on the impact suggested by the tree-like automata. Your choice creates an automaton from dependency graphs, and also shows how such an automaton can be used to detect and thus classify malware.
Malware, or in the case of malware, any file that intentionally harms a computer, network, or server. Types of malwareCommon programs include computer viruses, worms, Trojans, ransomware, and spyware.
Of course, research is underway to combine noise and dynamic malware analysis techniques to minimize the vulnerabilities of both. In the course of research, suchInvestigators like Islam et al. [13] should use static and dynamic methods here to better analyze and classify malware and its variants.
See Also
- History of computer viruses
Links
- ^ John von Neumann, Theory of Self-Reproducing Automata, Part 1: Transcripts of Lectures given at the University of Illinois, December 1949. Publisher: A. W. Burks, University of the United States, this 1966. Fred
- ^ Cohen, “Computer Viruses,” Ph.D. Dissertation, University of Southern California, ASP Press, 1988.
- ^ L. M. Adleman, “An Abstract Theory of Computer Viruses,” Advances in Cryptology — Crypto ’88, 403, Incs, pp. 354-374, 1988.

Malware or vindictive software is a program or archive that intentionally damages a healthy computer, network, or server. Types of malware include computer viruses, worms, Trojans, ransomware, and spyware.