Table of Contents
Approved
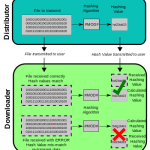
Recently, some drives have encountered a software checksum verification error code. This problem can occur for several reasons. Let’s discuss some of them below. The checksum is the actual value that is used to verify that a file is working or important transmission of information. In other words, it is the amount that checks the applicability of the data. Checksums are commonly used to compare two bandwidths to make sure they are the same for one person.
A checksum is a small block of wooden data derived from another block of digital data to detect errors that may have been introduced during transmission in addition to storage.
For maximum system security, always verify the checksum of any software package you download from the Internet before running it.
If you copy the fciv.exe file to the C:Windows directory, this command will work from any index drive on the command line. And
Display MD5, SHA1 And Blake2 Clicks For Windows Hashing..Fastest
The World’s Hashing App, Even Faster!

Welcome to Checksum, an incredibly fast and simple Windows file hashing application that generates and displays BLAKE2, SHA1 and MD5 hashes; often known as. “MD5 sums” or “fingerprints”; with a file, folder, or folder recursively, maybe even everything on disk, i.e. volume, it’s extremely fast, smartly simple, and. Many people firmly believe that this is the ideal hash utility on planet Earth.
Did I say fast? Not mind-boggling hash rates (much higher, even than the arguably fastest SSD), but the most efficient time to complete tasks. With control amounts, users indicate and clickHashed and hashed ones see files, directories, and even entire disks. Or checked. Easy. Quantity Check progress as work progresses. Click and go…
Available in a 64-bit version (also included is a 32-second version for Linux/UNIX/BSD or a simple Windows version).
Why?
In the ten years prior to my checksum verification, a bunch, maybe hundreds, of Windows MD5 hashing utilities had to be installed and uninstalled, and the vast majority of them muttered “Brain Dead POS!” under his breath, or words to that effect, or maybe not under his breath. firmly I knew that data validation should be easy, even easy, but often it turned out to be a chore.
Either these brainless programs don’t know about recursion or pretend they do, or they give MD5 hash papers stupid, generic names, or they won’t be able to handle long filenames, other people’s filenames are multiple, or files, they too work under MS DOS, either choke on UTF-8, or incredibly slow, insistent, or makes my life look like a complex interface, or doesn’t have decent hashing algorithms, or you don’tyou don’t even know how to sync delayed files with old ones, or you don’t have built-in integration or combination for these things in your life; and at the end I kept yelling “FFS! JUST DO IT!!!”.
Open a Windows Command Prompt. Hurry up: press Windows R , type cmd and hit enter.Navigate to the folder where the experts think the file has the MD5 checksum of which you want to check and analyze. You command: type cd followed by the specific path to papk.Type certutil -hashfile MD5
No more! Now it’s just that I set the checksum to one and it doesn’t suffer from any of these problems; as well as adding some national things.
Why Exactly?
Peace mind! The SHA1, blake2 and MD5 hashes are used to verify that virtually every filegroup or file remains unchanged. It’s so simple, useful, and even critical in just about any situation where data integrity is considered important.
For example, these weeks days MD5 hashes (and now less frequently SHA1 hashes) can be found next to downloads and even Windows purchase dates. When this hash is used, it ensures that the file you upload is exactly the same as the one submitted by the author and has not been modified in any way, added by a Trojan horse, etc.; In fact, a smaller change in critical information gives a completely different hash.
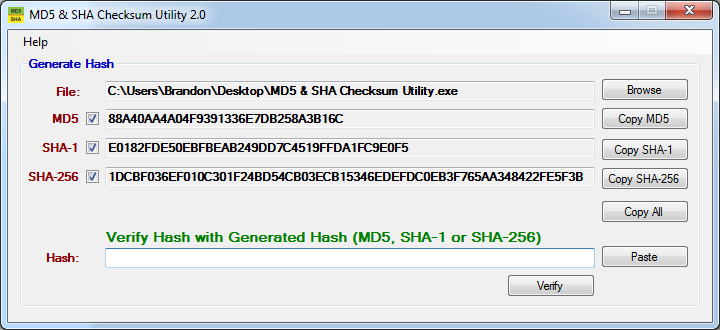
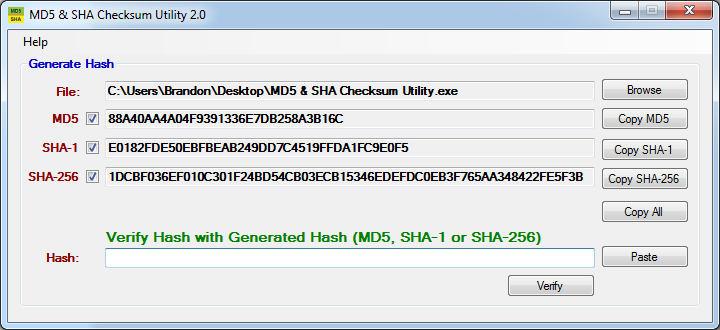
Unzip the downloaded zip file and publish the WinMD5.exe file. Click this Browse button, navigate to the house you want to view and select it. When you select a file, the tool will show you its MD5 checksum. Insert the original MD5 value as approved by the developer or purchaser.
A hash file is also better for checking whetherBut the 3D printed propeller blade has not been “redesigned” to successfully self-destruct!
This is also useful when you want to compare folder/directory files; and Checksum generation is much more accurate than a simple comparison of file sizes, dates, or any other property. easy easy checksum, file drag and drop Two for per-second hash comparison.
Open the checksum calculator if it didn’t open after installation.Click Browse next to the And View field to navigate to the manual entry you want to view.Select the type of checksum you are evaluating.Click the Calculate button.After clicking the “Calculate” button, the result will appear in our own results field.
If you burn a lot of data to CDs or DVDs, you can use a checksum to ensure the exact integrity of your data after burning and at almost any time thereafter. If your whole family is sharing data in some way, you can torrent your favorite files, run a file server, and/or just email a few files to your friends; However, the hashes give the technician at the other end the confidence that the file has arrived correctly and is 100% intact.
File Checksum is extremely easy to use. In the visual interface, select a file or sometimes a directory in your computer’s storage. The tool calculates and lists the checksum values. You can copy the information to the clipboard or export it to a CSV, XML, or TEXT file.
Digital fingerprints can not only provide reliable verification by an experienced processor for manipulation, virus attacks, damage to file backupscatches (and files), passport errors, etc. but, and serve as an “early warning” of possible media failures. , these objects are optical or magnetic. This is a hash error that has recently alerted others to poor quality batches of DVD-R discs; I saved time on disappearing data and got my hard drives refunded. I leave the rest of the millions of uses to the owners. However, there is only one reason; relaxed mind atmosphere.
Absolutely Actual File Check..
Open the checksum calculator in case it is not already open after general installation.Next to the launch box, click Browse and goto the shipment you want to view.Choose most of the types of checksums you will be testing.Click the Calculate button.After clicking the Calculate button, the result is displayed in a new results field.
Approved
The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today!

Checksum can create (two clicks, one or just drag and drop) or check (one click) against the hashes of a file, folder, or even a whole new disk full of files in addition to folders related to a simple, practical and efficient operation. Basically, you point to a file or folder and go there and ! Options are also controlled by command line switches, but most people don’t care; almost everything happens behind the scenes and is integrated into File Explorer popups (also ® known as “concept”, also known as “clickright-click”) (see Commands above).
Note. Not to mention checksum command line switches, this is NOT a Windows method
The software to fix your PC is just a click away - download it now.Open a command prompt window by clicking Start >> Run and right into CMD. Type exe and press Enter.Find the path to the sha256sum.exe application.Enter sha256.exe and enter the name of the file you are checking.The hit display can consist of 64 characters.