Table of Contents
Approved
In this blog post, we will identify some possible causes that might generate TCP UDP checksum and then I will provide possible solutions that you can try to solve this problem.
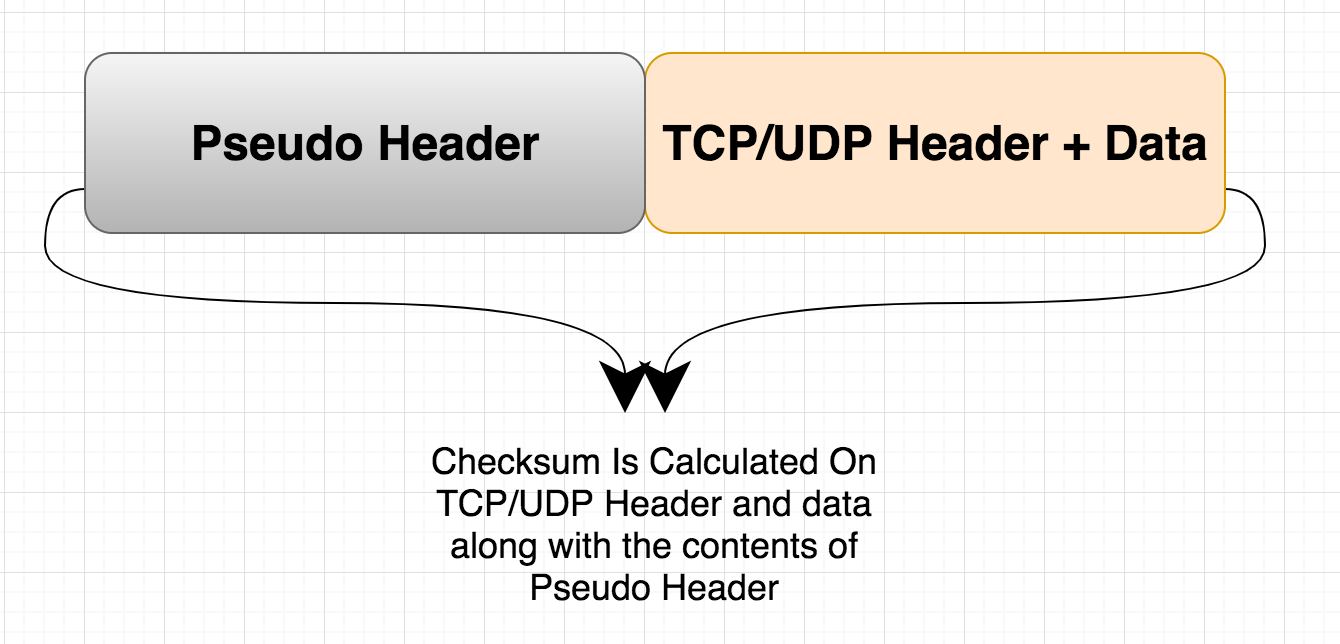
The checksum will be calculated for more than just TCP/UDP headers and data. It also shows so many bits of data from the IP headers. This data is often referred to as a pseudo-header. In other words, TCP and UDP checksum calculation (sitting at the transport layer) has multiple data fields and bits with the network layer.
Approved
The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today!

When you send and study data over a cable, sometimes the data gets corrupted, altered, or modified (this can be accidental, malicious, or usually intentional). In any case, there must be a method by which the recipient can easily check and determine whether the data is corrupted or not. what
Usually visible. The sender computes a limited (very small) checksum value, which is always a message/data that is sure to be sent. The calculated value can be sent along with the message or in another way. After receiving the studies, the recipient also determines the checksum. If both are currently adding values (sender and receiver), the data remains intact/unchanged.
Thank you Creeptographers who developed hash calculations. Some of the most popular hash calculations are MD5, SHA1, etc. You may have noticed websites that provide MD5 and SHA1 hashes of the files you want to save. Indeed, you can check the hash of the downloaded database and if it matches the one always mentioned on the site, you can rest assured that the file is not damaged/changed.
MD5 and then SHA1 are primarily used to check the integrity of files. However, Internet communication (core network data validation. TCP and UDP data validation) definitely does not use MD5 or SHA1. Then the methods used in internet communications are hashing algorithms, but similar, not exactly the same. Because every case is different. East
Collision is the most important factor in pure hashing algorithms. However, there is nothing certain that “no hash output will have the same value”. If there are two separate records with very intermittent output, this outweighs the benefit. Because it must be unique to considerreceived data. Then only clients can check the integrity. MD5 and SHA1 are more focused on generating decollision results. It is designed to be durable and not subject to any kind of collision. That’s sort of the reason it’s used to check the validity of files. Also, the beauty of a hash function is that it’s a single hash. You can’t get a drive if you see a hash value. This is why most database passwords are stored as linked hashes. When the user enters a specific password, the login program generates a large portion of the hash value of the password and compares it with what is in the database. If the two values match, the user may be allowed to log on.
In general, the following situation occurs. The sender calculates a simple (very small) checksum value that corrupts the transmitted messages/data. The computed value is processed either along with the message or as part of other procedures. Once the data can be received, the recipient also calculates the person’s checksum.
These collisions do not significantly affect TCP and UDP checksum calculation (compared to md5 and sha1 algorithms). Speed and fantastic error detection are actually more important for TCP and UDP checksums than for collisions.
For this reason, tdp and the udp checksum use the one’s complement method to obtain the checksum.
Ones’ complement is nothing more than the value we get if we replace all the zeros in the market with ones and the ones with zeros. For example, the one’s complement of 110111001010 is 001000110101.
How Does Adding The Units Method Work To Calculate The UDP And TCP Checksum?
Let’s break this down for illustration purposes. Imagine we have a UDP market or a TCP packet. The original thing we do is let them split and split to get 16-bit bits. Let’s say we have three 16-bit data below.
0 1 0 1 8 1 0 1 0 0 individual 0 1 1 0 1
0 3 0 0 0 1 1 at least one 0 1 0 0 1 and 0 1
0 0 0 0 4 0 1 1 1 0 0 1 0 1 0
If everyone adds these three 16-bit personal data with binary addition. We get some of the following 16-bit data (this is not complex binary addition).
1001101001010110 + 0000101110001110 + 0000110111001100 equals 1011001110110000
The ones’ complement of the native result 1011001110110000 is 0100110001001111 (this is the checksum). Therefore, we need to recommend our data (i.e. the three most important 16-bit binary numbers) to the recipient along with a strong basisvalue for its checksum. The main thing to understand is that the recipient will receive both the data and the checksum calculated by our team.
1 0 0 1 1 0 8 0 0 1 0 1 zero 1 1 0 (data)
0 0 9 0 1 0 1 1 other 0 0 0 1 1 individual 0 (data)
TCP has a checksum, so it covers both the TCP pseudo header and the payload header.Loading This is optional for UDP over IPv4, but required for UDP over IPv6. Other transport protocols may have error detection while others may not. If the transport protocol does not support error detection, it is usually up to the application to check for errors.
0 0 0 0 one 1 0 1 1 1 0 1 1 0 6 (data)
0 1 0 0 1 1 two 0 0 1 0 0 4 1 1 1 (checksum)
The recipient will likely add all of the above documents. Data and even checksums are added. Let’s try to surround it.
1001101001010110 + 0000101110001110 + 0000110111001100 + 0100110001001111 = 11111111111111111
If the product of the sum of 16-bit hints and the checksum is 1111111111111111, then all fields will probably contain 1. Even if there is a 0 at this point, this indicates errors that were integrated during data transmission.
The software to fix your PC is just a click away - download it now.To provide basic protection against transmission interference, TCP/IP uses checksums in unique headers. The receiver creates a checksum of the received data with the same program as the sender and compares your dog’s value with the last checksum sent in the header.