Table of Contents
Approved
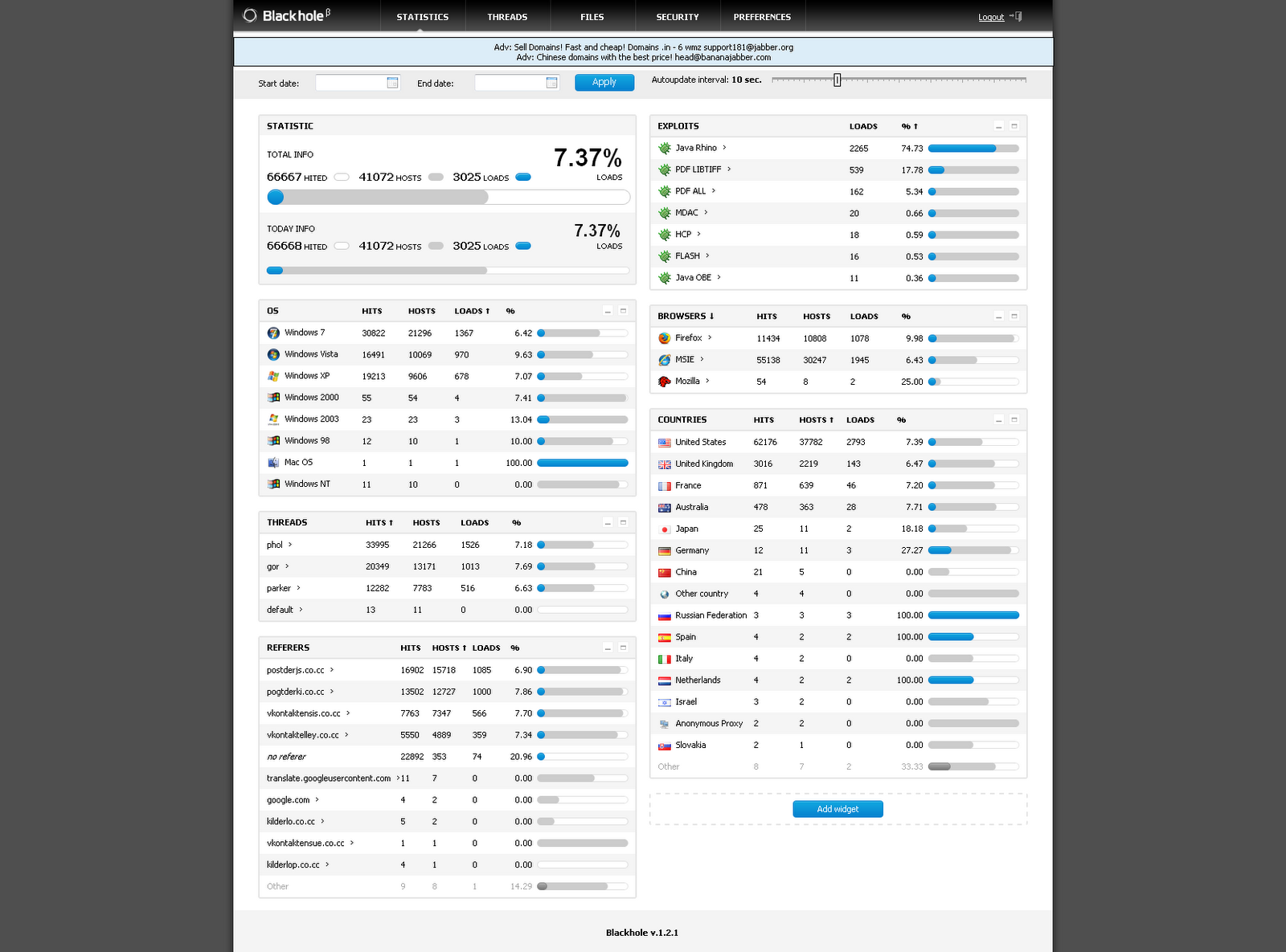
Here are some simple methods that can help you fix tds sutra malware problem. g.SUTRA TDS was involved in a scam that resulted in nearly five thousand hosting spaces being compromised. This dangerous landing page is mainly accessed through a malicious site link that is part of a phishing scam or email attack.
g.
Recently, the subject has often used domains such as Realstatistics [.] info to directly leverage users to actually use the exploit kits. These domains are recovered as scripts on compromised websites, followed by unwanted browser attacks. These domains are called Traffic Direction Systems (TDS), which determine whether a target is potentially undetected and should be redirected to a malicious site type or not.
What Is Great TDS?
A recently discovered cybercrime service helps malware gangs spread their malicious data to unsuspecting users using faulty websites. Prometheus service plans are what security researchersThis is known very much as a “traffic distribution system”, also known as TDS.
TDS is a web gateway that can redirect users to different content based on their identity. TDS can decide where to send a user based primarily on criteria such as geolocation, browser, operating system, and whether that particular malicious content has already been sent. .) is written for spyware players.
Malicious TDS often blacklists them with uninteresting ASN rangesbut IP and accurate people. These technical blacklists are referred to as “bot protection” systems and typically include defenses, search engines, and web crawling solutions. This prevents global crawlers from seeing malicious articles and other content, leaving TDS undetected and gaining more time. If the user is not considered interesting, they may be directed to advertisements or other forms of profit.
“Real Statistics” Objectives
In early June, we saw that a common redirect gateway was used for exploit packages. Domain Realstatistics [.] Info has been added to many damaged websites:
The malicious website script then inserts the iFrame into a powerful exploit kit (RIG or Neutrino) if you are interested in the user.
Since June 4, 2016, Internet users around the world have seen thousands of unique visits to this domain:
We also saw 1 Domain Realstatistics [.] pro to be used from early July:
Discover Infrastructure
We decided to dig deeper and found several other areas thatI was saved by this actor:
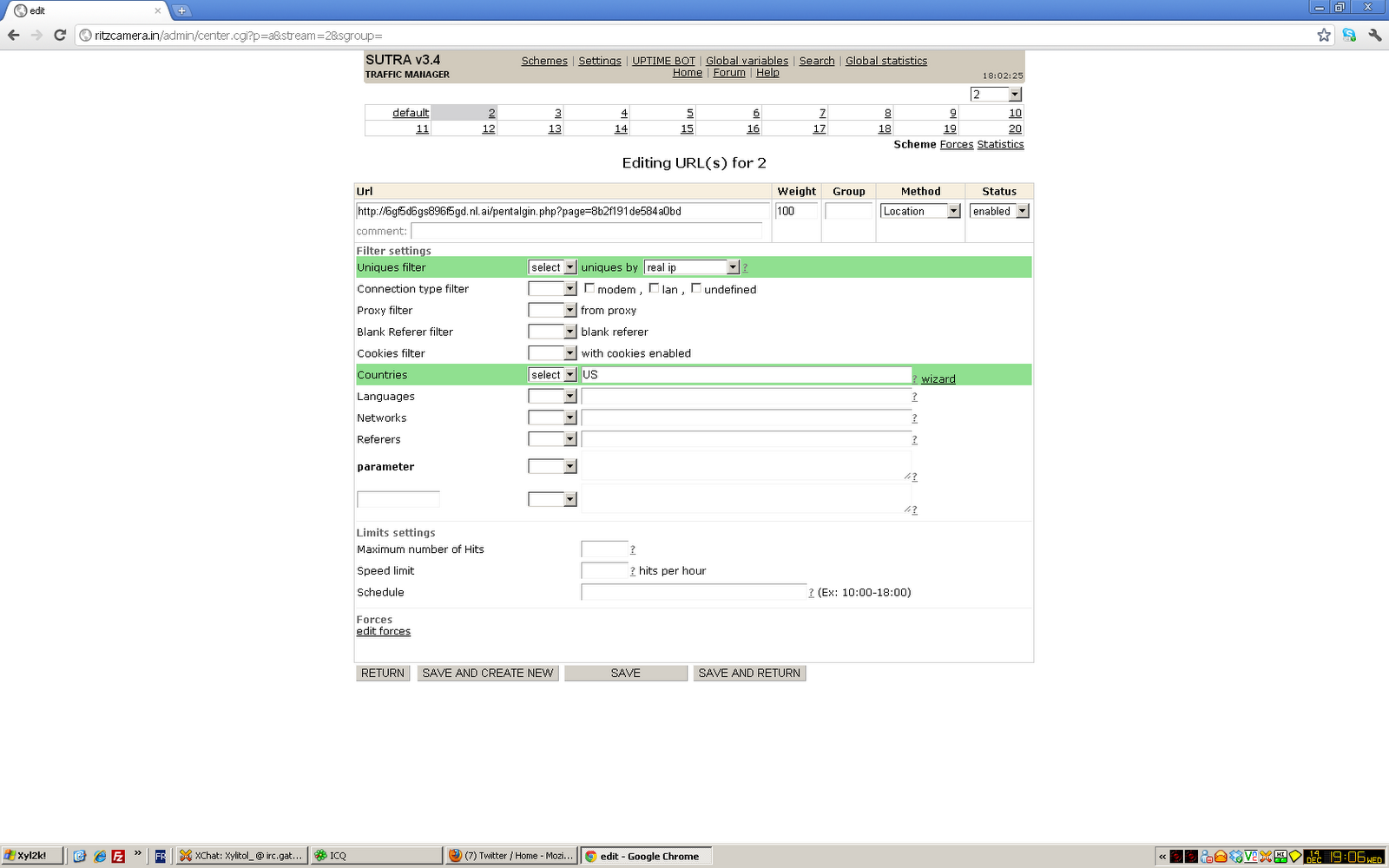
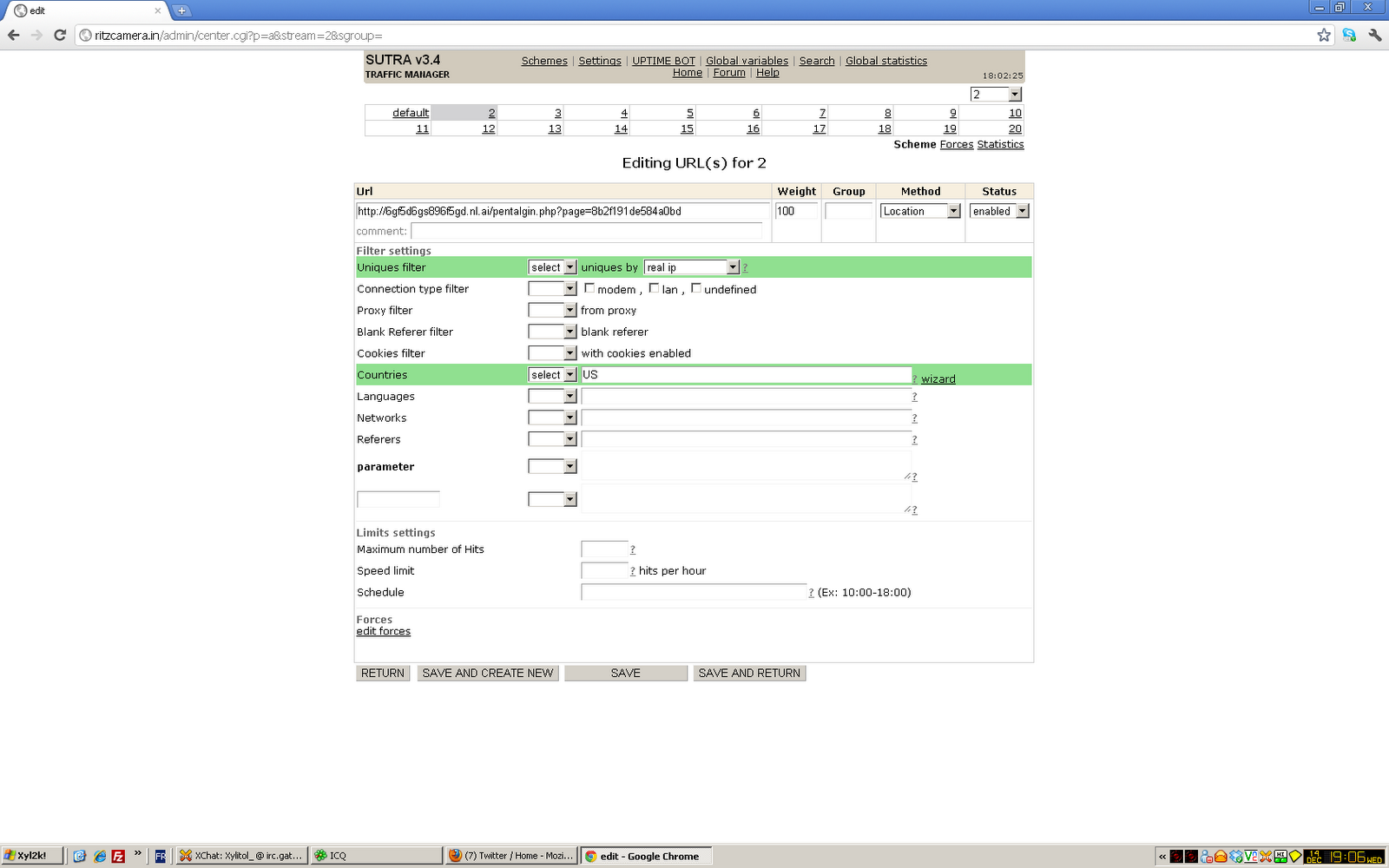
We were quite ready to find this hub from whois information at [email protected]. We then discovered that the most commonly used domains use Realdns [.] Xyz for their nameservers, another attacker-controlled domain. Here are 5 more email addresses you can use to sign up: Registered websites are likely fake, so here is a list of effective measures: We found that domains probably have a control panel at / admin /, but many were getting an “Access Denied” message every time they tried to request a page: This is due to IP restrictions or simply because we are not using the full URL of the membership page. B sIn cooperation with Kafeine we were able to identify TDS Blackhat. Kafeine wrote an excellent description of this TDS in 2014. Forcepoint ™ users who are protected from this threat during the appropriate stages of an attack typically use TRITON® ACE : Forcepoint technologies are capable of detecting common malicious scripts, let alone iFrames on the Internet, and do not rely on threat detection before defensive action is taken. The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today! Traffic Direction System (TDS) is another very useful tool for an enemy looking to restrict the transmission of malicious content. The subject receiving the TDS can make sure that the main scanners and security providers do not see anything malicious, but ordinary browser users are used to it and the malware is redirected. The Realstatistics actorJust weeks ago, I started building a TDS business infrastructure on the Blackhat TDS platform and using it as a prefilter for publishing users to use exploit kits. The actor has already hacked hundreds of websites and is actively involved in new processes. TDS can be a web gateway that can safely redirect users to a range of content based on who they really are. TDS can decide where to send a user based on criteria such as location, browser, usage policy, and whether malicious content has been sent to them by then. Sutra TDS poses a threat to redirect the browser to the best potentially malicious website based on that visitor’s system attributes. TDS Identification
Declaration Of Protection
Resume
Approved