Table of Contents
Approved
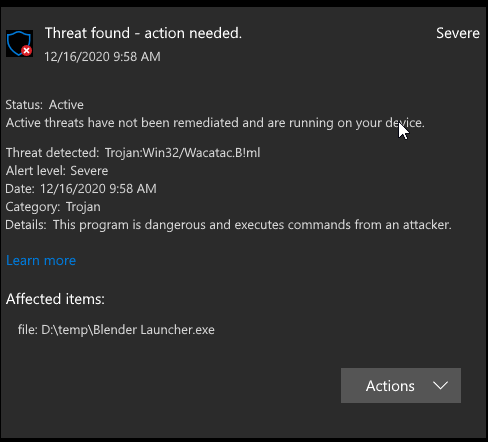
Sometimes your system may display a message stating that the trojan win32 almanahe b dll. There can be many reasons for this problem.
This Trojan horse enters the system as a file hosted by other viruses or as a file that users accidentally download when visiting malicious websites.
Arrival information
This Trojan enters the system, for example, in a file dropped by other spyware, or a file that was undoubtedly downloaded when users visit hated web -sites.
Removal procedure
p>
This Trojan currently removes the following files:
- % Windows% linkinfo.dll
(Note:% windows% is most of the Windows folder, usually C: Windows.)
Approved
The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today!

This story is generated by an automatic search engine.
Step 1
Before running a scan on Windows XP, Windows and Vista, Windows 7 users should preferably turn off Recovery to allow full scans of their computers …
Step 2
Find and remove e from file
Learn [More]
Some files can usually be hidden. Be sure to look for the “Find hidden files and folders” checkbox in the “Advanced options” option to include all music tracks and hidden folders in the search. % Windows% linkinfo.dll
Step 3
Scan your computer for a Trend Micro product and remove the files marked as recognized by TROJ_CORELINK.D. If the detected files have already been cleaned, deleted, or quarantined with a Trend Micro product, usually no further action is required. You can easily remove files from quarantine. You can find more information on this basic knowledge page.
Was this description helpful to you? Tell us how we did it.
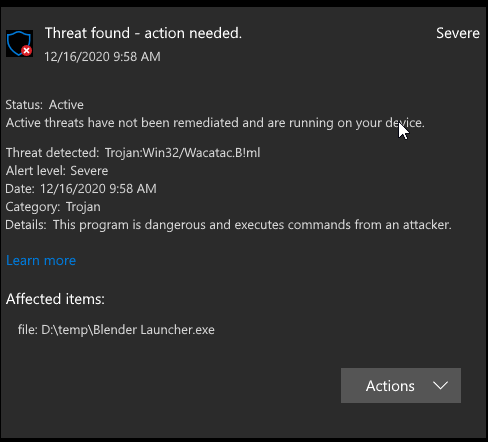
This Trojan is launched on the system as a folder hosted by other malware, or when a file has been unnoticed uploaded by interested parties while visiting malicious websites.
Arrival information
This Trojan is available on the system as a directory deleted by other malicious programs, or as a file downloaded without the knowledge of users visiting malicious websites.
Removal procedure
This Trojan removes the following files:
- % Windows% linkinfo.dll
(Note:% windows% is the Windows folder, usually C: Windows.)

This report was generated by an automated scanning system.
Step 1
Before multiple scans, Windows XP, Windows and Windows Vista Windows 7 users must disable System Restore to allow full scans. connected to their computers.
Step 2
Find and delete the above file
Learn [More]
Some files may be hidden. Be sure to activate cash verification No hidden files and folders using the Advanced Options option to successfully include all hidden files and directories in the search result. % Windows% linkinfo.dll
Step 3
Scan your computer with Trend Micro and delete files named TROJ_CORELINK.D will be detected. If the detected files have already been cleaned, deleted, or quarantined with a Trend Micro product, no additional path is required. You can also just delete files from quarantine. Visit this valuable basic knowledge page for more information.
Was this description helpful to you? Tell us how we lived in America.