Table of Contents
If you have spyware and malware on your system, we hope this guide will help you.
Approved
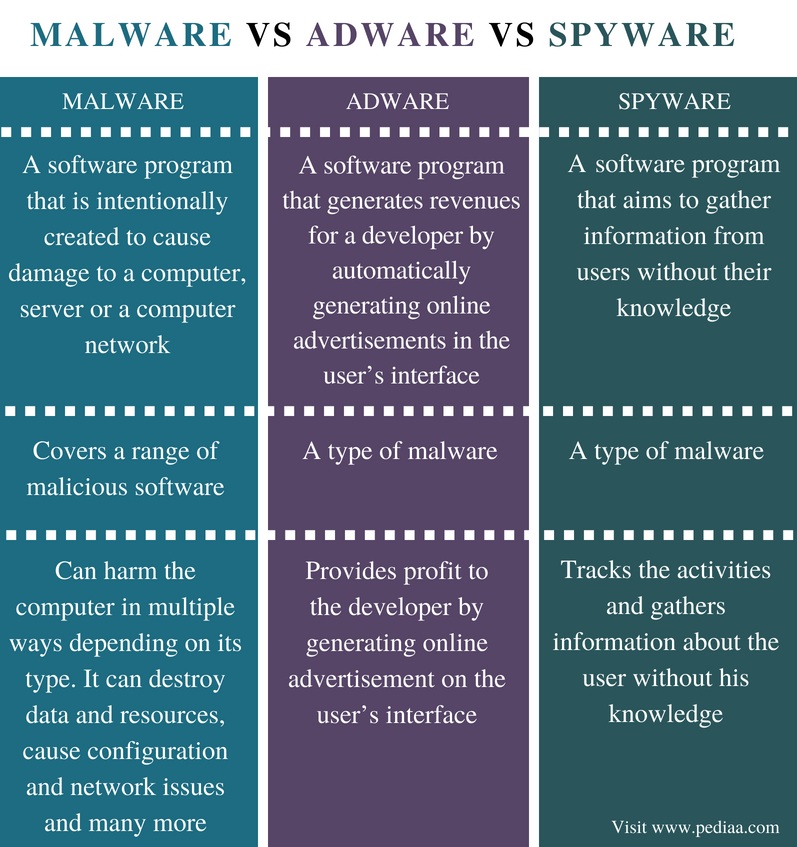
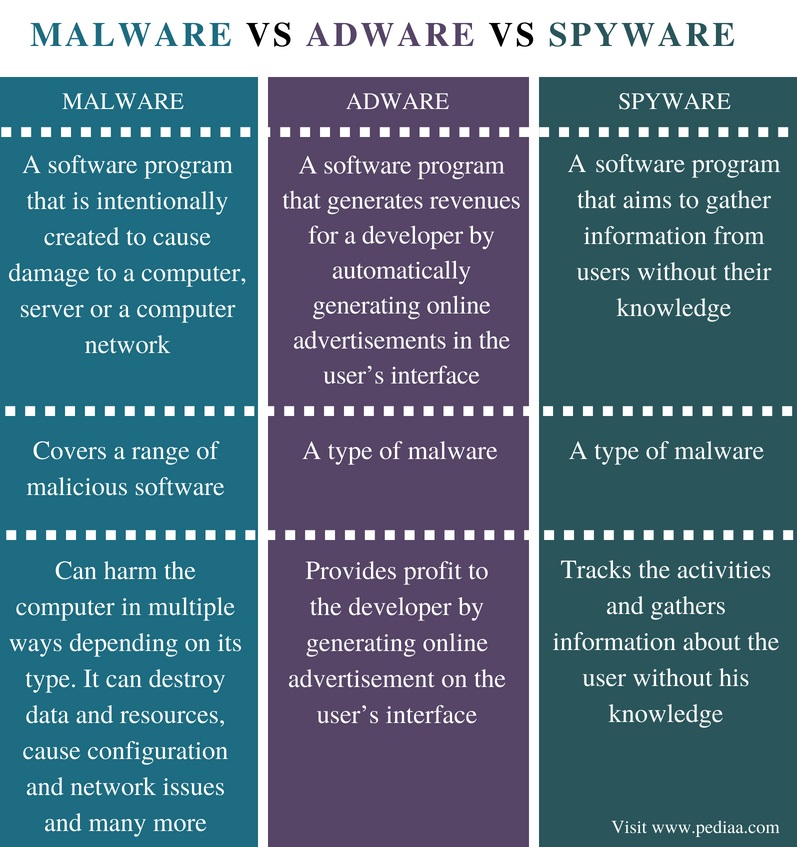
Spyware is basically a collection of technologies that helps collect information about a computer user without their knowledge. Adware is software that displays pin ads while running. Malware is software that is considered harmful to the computer user in the form of viruses or spyware.
This site URL provides an overview of most popular malware applications. For specific calculations for malware protection, see our Virus and Security Threat Protection pages.
What Is Malware?
Malware is a collective term used to describe a collection of malware, including fake viruses, adware, user spyware, hacker software, and related security software.
Once installed on your computer, these programs can seriously affect your privacy and the security of your computer. For example, malware is known to transmit financial information to advertisers and others without the user’s consent. Certain workouts are also known to contain parasites and viruses that can seriously damage your computer.
Types Of Malware
- Viruses are the most common and potentially most destructive type of malware. They can do anything from deleting data on your computer to hacking into your computer to shutdown other systems, sending spam, or distributing illegal content.
- Spyware collects personally identifiable information and transfers it to interested third parties without the knowledge or consent of your company. Spyware is known to install Trojan horse viruses. Advertisements
- Contextual advertising on the Internet.
- Illegal security software has a legitimate purpose to force you to open your system to other infections, provide confidential information, or pay for unnecessary or even harmful “cleanup”.
- Attackers alter your browser settings (for example, on your home page and toolbars) to displayThey pop-up advertisements and create new shortcuts for personal computers. It can also communicate your new personal preferences to the interested parties listed below. About
Malware Facts
Malicious software is often bundled with other software and can be attached without your knowledge.
For example, AOL Messenger Instant comes with WildTangent, a stored malware. Some peer-to-peer (P2P) blogs like KaZaA, Gnutella, and LimeWire also combine spyware and adware. Although end user license agreements (EULAs) usually contain information about additional software, some malware is automatically installed without user notification or consent. East
Malware is very difficult to remove. Programs
Malware is difficult to remove in the usual way. They also “hide” in unexpected places on your computer (for example, you may need to reinstall your operating system to completely remove the most common infections.
Approved
The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today!

Malware threatens your level of data protection.
Malware is known to leak personal information from time to time and help you deal with advertisers and other third parties. The most common information collected includes your family’s browsing and shopping habits, your computer’s IP address, or your consent information.
Malicious software compromises the security of your computer.
Some types of malware contain files commonly referred to as Trojans. Others make the computer vulnerable to viruses. Regardless of the type, malware is known to directly or indirectly cause viral infection, conflicts with legitimate software and compromises the basic security of every operating system, Windows and Windows, and the other Macintosh.
How Do I Know If My Computer Has Malware?
Browser Crashes And Instability
- Browser closes unexpectedly or stops responding. Home
- page goes directly to another website and cannot be reset.
- In brownzer added new toolbars.
- If you click on the link, it will not work or you will be taken to a new independent website.
The
Poor System Performance
- The internet connection was unexpectedly interrupted.
- The computer stops or takes longer to start.
- Applications do not open or even the loading of the latest (especially security software) is blocked.
- New icons are intended to make it easier to install desktop or suspicious programs.
- Some system settings or configurations are not available to potential customers.
Advertising
- Ads appear even if the main browser is not open.
- Browser opens for ads.
- New pages only open in the browser for ads. Results
- Only ads are shown on search sites.

Security threats exist in all states. The threats we’re focusing on this time around accidentally launch applications called adware, spyware, and malware. If you are usingIf you have a computer system that has Internet access, you are likely to become infected with this type of task. To help you, our staff has given a short definition of each of them.
Adware is software that generates advertisements such as pop-ups or hyperlinks on web pages that are never part of the actual web page.
Spyware is software that collects and sends certain information and information about user behavior, with or without permission. It is sometimes believed that permission to collect and distribute on the market was obtained simply by installing software or reloading a web page.
Malware is shorthand for malware. It turns out that it is very different, but its main purpose is to really harm your personal computer. The damage can be different. Typical models of malware are computer viruses and worms.
How did you find it?
There are many ways to get infected with adware, spyware, adware and spyware. Most slInfection occurs without your knowledge.
- It can be installed with another program. Many freeware programs install others as spyware. With the same success it is possible not to say that this is so. When voiced, do so in accordance with the license agreement.
- It can be placed behind your back when you visit a website or click on a functional link, including sponsored links, or when you tell men and women that you won something.
- Sometimes a good email or website can make you think you can download something to see what they have to offer. For example, an email might say that someone sent you an electronic greeting card, but you need to download a special viewer to read it, or the website says nicely that you have a special “media player” – View on their website.
- It can claim to prove something important, useful, or desirable: spyware can disguise itself as typical security, warnedno, “free malware scan” or even a deadline for spyware removal that you can click on.
What is he doing?
Spyware does everything from annoying to criminal and malicious. It can do everything, but also all of the following:
- Are you using the system resources, memory and bandwidth of your good computer, and are you slowing down your computer and / or your internet connection?
- Remove, modify, or disable core software, folders, programs and services related to aspects of Windows and.
- Use worms, trojans, and therefore backdoors to open your computer to further attacks, and these programs are also great at installing software that allows your new computer to be the “host” that may now be well known after “ bot “. Bots Sending, collecting and analyzing information from laptop computers around the world is quite normal.
- Use your computer to send spam – yes, really! It is estimated that 80% of spam inour world is sent from zombie computers infected with “Trojan spam”, exactly what was installed by spyware with potentially possible worms.
- A conflict with other programs causing your computer to crash or freeze.
- Hide the specific presence of other pests and record them when you try to avoid them.
- Install “keyloggers” that log keystrokes, that is, log everything that people enter.
- Steal your passwords, credit card manual and other personal information to steal identity.
- Track your browsing habits and record the pages of the website you visit. They return this collected data to their manufacturers for verification and sale to other companies.
- Also enter your email address for special access to spam (junk mail).
- Irritates you with pop-up ads on TV, even if pop-ups are blocked in your web browser.
- Hack your browser and change your home zone, add favorites / bookmarks or Redirect to other websites without your permission. Typically, you will be redirected to websites that are billed for each visit.
The ability of spyware to make sure you do all of these things poses a real threat to the security of your precious computers at work and at home. This can lead to data loss, damage to legitimate software, slower network writes, decreased performance, and in the worst case, identity theft.
How to avoid a choice?
- Do not install anything that you are not usually familiar with, especially if the person has not specifically researched it, and just download the software yourself. No
- Click on any ads, offers, security warnings or “You Win!” On web blog pages, especially those that appear in pop-ups.
- Check the Internet for spyware before installing unfamiliar software.
- Try to constantly visit verified websites.
What if youthink your work computer is infected
If you suspect that your company’s computer systems may be infected, please contact technical support by phone (x6137), ![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()