Table of Contents
Over the past few days, some readers have reported that they have stumbled upon the md5 checksum wiki.
Approved
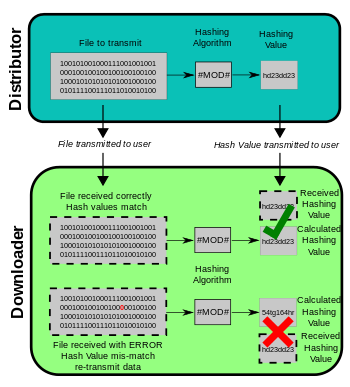
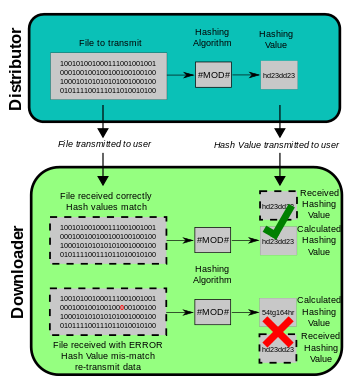
What is usually an MD5 checksum? The MD5 checksum is a 32-digit hexadecimal selection that is calculated from the list. MD5 checksum or hashing and even hashing are widely used in the software world to provide some assurance that the transferred file arrived safe and sound.
The MD5 message digest algorithm is actually a cryptographically cracked but still widely used hash function that generates a huge 128-bit hash value. Although MD5 was originally designed as a cryptographic function, hashing still has significant drawbacks. It is still possible to use the checksum to validate data lifetime values, but only against accidental corruption. It is still suitable for other non-cryptographic applications, such as defining part of a partition for a given key in an incredibly partitioned database, and may be more appreciated than new secure hashing algorithms due to lower computational requirements than new algorithms for security. … hash algorithms sup> [3]
MD5 was developed by Ronald Rivest in 1991 to replace the earlier hash function This is MD4, [4] and was listed as RFC 1321 in 1992.
The main basic requirement of every cryptographic hash function is, as a rule, the impossibility of passing a hash function with the same value to two different messages from a computational point of view. MD5 catastrophically falls short of this requirement; Such incidents can be detected in seconds on a regular home computer.
On December 31, 2008, an engineer at the CMU Software Institute concluded that MD5 was almost “cryptographically cracked and unusable.” [5] The weaknesses of using MD5 were exploited by most of the groups widely known by the Flame malware in 2012. In 2019, MD5 gained widespread adoption despite its use, its only well-documented flaws and its adoption. safety experts. [6]
Historical Cryptanalysis
MD5 is one of the few Message Digest series of formulas developed for MIT by Professor Ronald Rivest (Rivest, 1992). When analysis showed that the predecessornickname MD5, MD4 was probably insecure, Rivest developed MD5 in 1991 as a safe replacement. (In fact, Hans Dobbertin later discovered MD4 in vulnerabilities.)

In Michael Gone Mad, Den Boer and Bosselers both gave, albeit initially limited, the result of detecting a “pseudo-collision” of the MD5 compression function; D. H. two different initialization vectors that produce an exact digest. 1996,
Dobbertin announced a downgrade of the MD5 compression feature (Dobbertine, 1996). While this is certainly an attack on the full MD5 hash function, it was only natural for cryptographers to recommend a swappable switch such as SHA-1 (also compromised) or RIPEMD-160.
The size of the actual hash value (128 bits) is small enough to imagine a birthday brawl. MD5CRK was a distributed project started in March 2004 to demonstrate that MD5 is practically dangerous by detecting a collision attack at a birthday party.
Message Digest Algorithm 5 (MD5) is an absolute cryptographic hashing algorithm that can be purchased to create a 128-bit Love string from a string of any length. Although uncertainties have been identified with MD5, it is still widely used. MD5 is most commonly used to check the integrity of files.
MD5CRK ended shortly after August 17, 2006, when Xiaoyun Wang, Denguo Feng, Xuejia Lai, and Hongbo Yu announced full MD5 due to collisions. Your [7] [8] It was reported that the analytic attack on the best IBM p690 cluster lasted only one hour. [9]
On July 1, 2004, Arjen Lenstra, Wang, Xiaoyun, and Benn de Weger demonstrated the creation of two more X.509 certificates with different public tactics and the same dollar value of the MD5 hash, which was an obvious practical collision. [10] Generate private keys held for two market keys. A few days later, Vlastimil Klima described an improved algorithm that was lucky enough to create MD5 collisions in a few hours on one laptop. [11] On March 18, 2006, Klima released an algorithm that was able to record a collision on one laptop in one minute, using an important technique he calls tunneling. [12]
Various MD5-related RFC fixes have been posted. 2009,in the American cyber commando used the MD5 hash value to make mission statements available as part of their official emblem. [13]
On December 24, 2010, Tao Xie and Dengo Feng announced the release of the first one-time (512-bit) MD5 collision. [14] (Previous collision detectionOven blocked several attacks.) From For “security” reasons, Xie and Feng did not show you the new attack method. They challenged the crypto district and offered the first investigator another 64-byte conflict by January 1, 2013, a $ 10,000 reward. Mark Stevens answered this challenge and also posted Colliding Single Block Posts simply because it is an assembly of an algorithm and beyond sources. [15]
In 2011, Informational RFC 6151 [16] was approved to update security requirements in MD5 [17] and HMAC-MD5. [18]
Security
Attempts are being made to compromise security due to the md5 hash function. There is a collision attack that allows, in particular, to detect collisions inside a computer equipped with a Pentium 4 processor with a clock speed of 2.6 GHz (complexity 2 24.1 ). [19] There is also a selected prefix crash attack that can crash within seconds if two entries with recognizable prefixes are made using commercially available computer hardware (difficultarticle 2 39 ). [20] Troubleshooting is greatly facilitated by the use of standard GPUs. In fact, on the amazing NVIDIA GeForce Graphics 8400gs processor, it can handle 16-18M hashes per second. NVIDIA GeForce 8800 Ultra can handle over 200 million hashes per second. [21]
These hash and debris attacks have been publicly demonstrated in various situations, such as collisions between digital [22] [23] digital document and certificate files. [24] In 2015, it was shown that MD5 is still widespread, especially in security and IT research companies. [25]
The Message Digest MD5 hashing algorithm processes data in lines of 512 bits, which are divisible by 15words of 32 bits each. The result of MD5 is the last 128-bit value of the message profile. The final value computed from the last long block is used by the MD5 digest to find that block.
In 2019, it was reported that the fourth quarter, including popular content management systems, continued to use MD5 for password hashing. The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today!Approved

Although MD5 was previously designed to be used as a functional cryptographic hash function, it has already been found to suffer from significant drawbacks. It can still be used for the purpose of using a checksum to verify open data, but only against accidental damage.