Table of Contents
Today’s guide has been created to help you when you receive an anubis Malware Scanner error code.
Approved
Description Of The Anubis Trojan
The Anubis Trojan is almost certainly a banking Trojan that is managed to infiltrate the Google Play Store and is designed to infect Android devices after it has been placed on the victim’s device with a Trojan Downloader. As soon as the Anubis trojan gets inside the device, it starts its nasty tasks like recording sound, encrypting some files from any device external storage, neighborhood tracking, collecting PayPal referrals, sending SMS spam and this collection of these users includes credentials for online -banking. and additional information. The Anubis Trojan also locks the screen of the device itself, turning it slightly black and allowing access to the infected device via the RAT backdoor. The Anubis Trojan can take screenshots of the device screen when the user of the device logs into the application.
So What Is Anubis?
No, this unique article is not about the ancient Egyptian god of embalming and the dead. Anubis is a banking trojan and update bot obtained from Maza – in a leaked banking source code.The Trojan we reported on earlier this year.
It’s Anubis Malware: Banking Trojans Explained
PCRisk discussed some of the spoofing strategies that attackers use to install Anubis malware to the device. Users are advised to stay away from any websites or applications using these indicators.
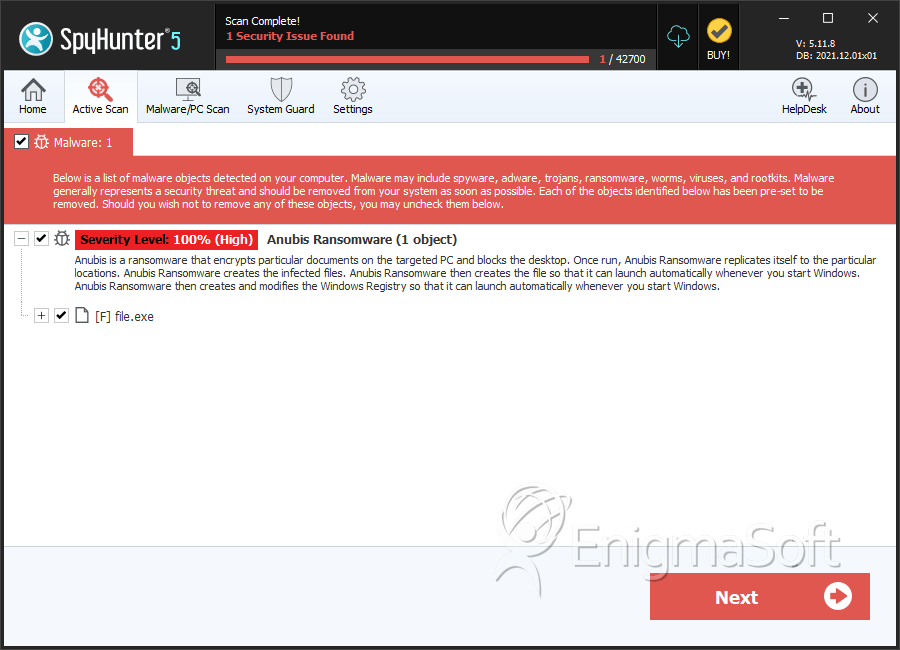
Anubis Ransomware Description
Anubis Ransomware is almost certainly a new variant of the popular open source EDA2. This could be dangerous ransomware that encrypts the victim’s user files and applies the encoded extension file to the victim’s bandwidth. The most common file categories are affected, including the following:

Anubis
Anubis was considered malware capable of stealing important personal information from your device and damaging important archives, corrupting your software. and even apply ransomware on your system. According to experts’ warnings, Anubis is classified as a Trojan horse and should be removed immediately.
Who Are The Actorsthreats And How Is Anubis Literally Being Used?
Anubis is primarily about banking. Trojan. Therefore, its default function is to keep track of an appropriate number of “destination applications” that are of great value for obtaining personal information or credentials for financial purposes. Target applications are hardcoded by the package name in the source client.
Approved
The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today!

What Is Flooder.Anubis?
Flooder is a form of computer virus that allows attackers to literally flood a specific target with a large amount of traffic and data. They are often used to block connections or simply interrupt normal communication between users.
What Is Anubis Sandbox?
Using Anubis Email Security Services. By now adding a Brief Sandbox to your security, a person is adding a great additional partial protection, useful for detecting this latest malicious code by detecting its use on an isolated computer equipped with the latest anti-sandbox programs – / Anti-VM pdesigned against – measures.
The Era Of Mobile Malware Downloaders
As app store operators remove security from those associated with malicious developers. Efforts to ensure that distributors of black apps do not bypass the path to them. To bypass the ever-changing app store defenses, mobile adware and vendors are using a PC malware strategy: instead of uploading the actual malware to the app store, which leads to predation and detection very early in the distribution chain, they upload a downloader, which may seem harmless compared to possible malware.
The software to fix your PC is just a click away - download it now.