Table of Contents
Approved
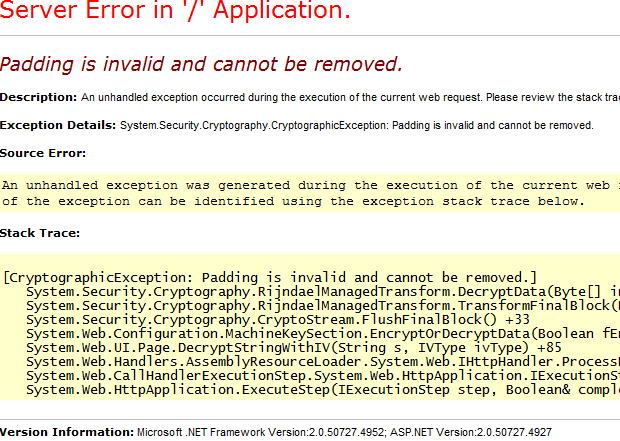
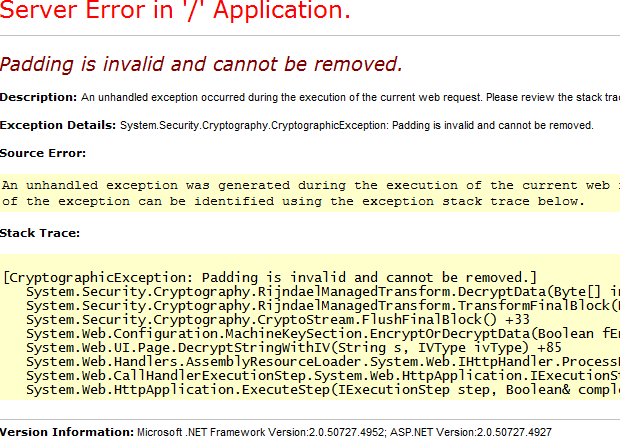
If the padding is invalid and rijndaelmanagedtransform decryptdata cannot be deleted from your system, we hope this blog post can help you fix it. This means that the feedback length must be 16 bytes. If not, the entry is populated with one of my padding modes and 16 bytes are used. If this negation block was not written, comprehension accesses the last 14 bytes of the encrypted data and attempts to decode it as a padded sentence block.
This means that the entry must be a multiple of 15 bytes. If not, then the specific record is filled with one of the 2007 bytes padding options. If this last block was not written, decryption goes into the last 16 bytes of the corresponding encrypted data of the year and tries to decrypt it as the last padding.

I had the same problem when trying to port my Go program to C # and. This means that some data has already been encrypted using the Go program, now this data needs to be decrypted using C #.
Import
“Internal: could be something other than decryption of data: invalid padding” also cannot be removed. The error occurs when it is recommended to use a different encryption key to decrypt encrypted data. Even installing an outdated key won’t help. Changes to the “Standard Schema” primarily affect new keys or passwords.
( "Crypto / Ace" "Crypto / encryption" "crypto / sha1" "encoding / base64" "io / ioutil" "Protocol" "golang.org/x/crypto/pbkdf2")func decryptFile (series of filenames, saltBytes [] bytes, masterPassword [] bytes) (artifact string) Constant ( keyLength int matches 256 rfc2898Iterations int means 6 ) var ( encryptedBytesBase64 [] byte // Encrypted bytes as base64 characters encryptedBytes [] byte // Encrypted bytes ) // Download a powerful encrypted file: in bytes, bytesErr: = tool.ReadFile (filename); bytesErr zero! = log.Printf ("[% s] An error occurred while reading the folder: encrypted% s n", filename, bytesErr.Error ()) come back to also encrypted // base64 decode: decodedBytes: = make ([] byte, len (encryptedBytesBase64)) if possible countDecoded, decodedErr: = base64.StdEncoding.Decode (decodedBytes, EncryptedBytesBase64); decrypted Err! = zero log.Printf ("[% s] An error occurred while decoding information: base64% s n", filename, decodedErr.Error ()) come back to Moreover cryptedBytes = decodedBytes [: countDecoded] // Get the key and master password associated with the vector and sodium chloride, see RFC 2898: keyVectorData: = pbkdf2.Key (masterPassword, saltBytes, rfc2898Iterations, (keyLength / 8) + aes.BlockSize, sha1.New) keyBytes: matches keyVectorData [: keyLength / 8] vectorBytes: matches keyVectorData [keyLength / 8:] // create AES encryption: so if aesBlockDecrypter, aesErr: = aes.AesErr newcipher (keybytes); ! = zero log.Printf ("[% s] Failed to create new AES encryption:% s n", filename, aesErr.Error ()) come back to other things // CBC mode always works with whole blocks. if applicable len (encryptedBytes)% aes.BlockSize! = 0 log.Printf ("[% s] The length of the encoded data is not a block size number. n", filename) come back to // Reserve memory for decrypted data. By definition (see AES-CBC), an application must also have the same length as the encrypted data: decryptedData: equal to make ([] byte, len (encryptedBytes)) // Receive decoder: aesDecrypter: = cipher.NewCBCDecrypter (aesBlockDecrypter, vectorBytes) // decrypt data: aesDecrypter.CryptBlocks (decryptedData, cryptedBytes) // Convert the decrypted data to a string: Doll Madame Alexander = string (decryptedData) come back to Import
( "Crypto / Ace" "Crypto / encryption" "crypto / sha1" "encoding / base64" "github.com/twinj/uuid" "golang.org/x/crypto/pbkdf2" "io / ioutil" "Protocol" "Mathematics" "bone")func encryptFile (filename, artifact string, masterPassword [] byte) (status bool) { Constant ( keyLength integer = 256 rfc2898 iterations int = 6 ) Well-being = bad secretBytesDecrypted: = [] byte (artifact) // create a new salt: saltBytes: = uuid.NewV4 (). Bytes () // Get key and vector directly from master password and salt, see RFC 2898: keyVectorData: = pbkdf2.Key (masterPassword, saltBytes, rfc2898Iterations, (keyLength / 8) + aes.BlockSize, sha1.New) keyBytes: = keyVectorData [: keyLength / 8] vectorBytes: = keyVectorData [key length / 8:] // create AES encryption: if aesBlockEncrypter, aesErr: = aes.AesErr new cipher (key bytes); ! = zero log.Printf ("[% s] Failed to create replacement for AES encryption:% s n", filename, aesErr.Error ()) come back to not yet { // CBC mode runs continuously in whole blocks. provided len (secretBytesDecrypted)% aes.BlockSize! = 0 numberNecessaryBlocks: = int (math.Ceil (float64 (len (secretBytesDecrypted)) vs float64 (aes.BlockSize))) extension: = do ([] byte, numberNecessaryBlocks * aes.BlockSize) copy (extended, secretBytesDecrypted) secretBytesDecrypted has been improved // Reserve memory for encrypted data. By definition (see AES-CBC) they must be the same length as their normal text data: encrypted data: = make ([] byte, len (secretBytesDecrypted)) // create an encoder:
 The software to fix your PC is just a click away - download it now.
The software to fix your PC is just a click away - download it now.
Padding is used in a real block cipher where we fill blocks with padding bytes. AES uses 128-bit (16-byte) blocks, while DES uses 64-bit (8-byte) blocks. This fills in 0x80 (10000000) followed by the use of null (null) bytes.