Table of Contents
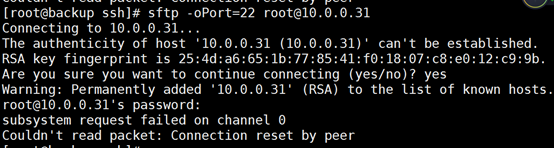
If the sftp subsystem request fails, this article will help you.
Approved
Connecting to ussecvmpalisap1 …
OpenSSH_4.7p1 + sftpfilecontrol-v1.2-hpn12v17, OpenSSL 0.9.7m Feb 23, 2007
HP-UX Secure Shell-A.04.70.010, HP- UX Secure Shell Version
debug1: read configuration data /u09/ps/pspro/.ssh/config
debug3: encryption ok: aes128-cbc [aes128-cbc, 3des-cbc, blowfish-cbc, cast128- cbc, arcfour, aes192-cbc, aes256-cbc]
debug3: encryption ok: [aes128-cbc, 3des-cbc, blowfish-cbc, cast128-cbc, arcfour, aes192-cbc, aes256-cbc]
debug3: 3des -cbc encryption now: Blowfish-cbc [aes128-cbc, 3des-cbc, blowfish-cbc, cast128-cbc, arcfour, aes192-cbc, aes256-cbc]
debug3: encryption ok: cast128-cbc [ aes128 – cbc, 3des-cbc, blowfish-cbc, cast128-cbc, arcfour, aes192-cbc, aes256-cbc]
debug3: cipher ok: arcfour [aes128-cbc, 3des-cbc, blowfish-cbc, cast128- cbc, arcfour, aes192-cbc, aes256-cbc]
debug3: code as follows: aes192-cbc [aes128-cbc, 3des-cbc, blowfish-cbc, cast128-cbc, arcfour, aes192-cbc, aes256 – cbc]
debug3: encryption ok: aes256-cbc [aes128-cbc, 3d es-cbc, blowfish-cbc, cast128-cbc, arcfour, aes192-cbc, aes256-cbc]
debug3: Encoding ok: [ aes128-cbc, 3des-cbc, blowfish-cbc, cast128-cbc, arcfour, aes192 -cbc, aes256-cbc]
debug1: read computer configuration files / opt / ssh / etc / ssh_config
debug3: RNG ready and does not stop seeding
debug2: ssh_connect: needpriv 0
debug1: direct connection to port 22 ussecvmpalisap1 [199.52.50.79]
debug1: connection established.
debug3: no RSA1 key file /u09/ps/pspro/.ssh/id_dsa_1.
debug2: key_type_from_name: unknown key type ‘—– BEGIN’
debug3: not often known key_read: key typeand
debug3: key_read missing: space
debug3: without key_read: space
debug3: key_read missing: space
debug3: key_read missing: space
debug3: key_read missing: space
debug3 : key_read moved: space
debug3: key_read missing: space
debug3: shed key_read: whitespace
debug2: key_type_from_name: unbeka nnter key write ‘—– END’
debug3: key_read missing: keytype
debug1: ids file for /u09/ps/pspro/.ssh / id_ dsa_1 type 2
debug3: optional RSA1 file /u09/ps/pspro/.ssh/id_dsa_2.
debug2: key_type_from_name: reproduce unknown key ‘—– BEGIN’
debug3: key_read: key type missing
debug3: key_read: key_read lost: space
debug3: key_read missing: space
debug3: not enough key_read: space
debug3: missing key_read: space
debug3: without key_read: space
debug3: missing key_read: space
debug3: keep key_read: space
debug3: missing key_read : space
debug3: key_read required: space
debug3: missing space
debug2: key_type_from_name: unknown key type ‘—– END’
debug3: key_read: key required type
debug1 : identity file /u09/ps/pspro/.ssh/id_dsa_2 type 2
debug3: non RSA1 key file /u09/ps/pspro/.ssh / id_dsa_3.
from ebug2: key_type_from_name: unknown key type ‘—– BEGIN’
debug3: key_read: shifted key type
debug3: key_read: missing key_read: space
debug3: missing т key_read: whitesp ace
debug3: missing key_read: space
debug3: none key_read: space
debug3: missing key_read: space
debug3: key_read required: space
debug3: missing key_read: space
debug3: removed key_read: space
debug3: missing key_read: space
debug3: space required
debug2: key_type_from_name: unknown key mode ‘—– END’
debug3: key_read : key type missing
debug1: identifier declaration / u09 / ps /pspro/.ssh/id_dsa_3 type 2
debug3: No RSA1 in base file / u09 / ps / pspro / .ssh / id_dsa_4.
debug2: key_type_from_name: unknown key types ‘—- – BEGIN’
debug3: key_read: missing key type
debug3: key_read: waiver key_read: whitespace
debug3: missing key_read: whitespace
debug3: leave key_read: whitespace
ru bug3: missing key_read: whitespace
debug3: leave key_read: whitespace
debug3: missing key_read: whitespace
debug3: not often known key_read: space
debug3 : missing key_read: space
debug3: key_read not eating: space
debug3: missing space
debug2: key_type_from_name: incognito key type ‘—– END’
debug3: key_read: missing key type
debug1: identity file / u09 / ps / pspro /.ssh/id_dsa_4 2
debug1: enter remote protocol version 2.0, remote software performance WRQReflectionforSecureIT_7.2 Build 151
debug1: Match: no WRQReflectionforSecureIT_7.2 Build 151
debug1: enable 0 compatibility mode for protocol 2.0 only
debug1: local version string SSH-2.0-OpenSSH_4.7p1 + sftpfilecontrol-v1.2-hpn12v17
debug2: fd parameter 4 O_NONBLOCK
debug3: RNG was ready to hop download
debug1: SSH2_MSG_KEXINIT sent by debug 1: SSH2_MSG_KEXINIT received
debug2: kex_parse_kexinit: diffie-hellman-group-exchange-sha256, diffie-hellman-group-exchange-sha1, diffie-shamanhell- group14 group1-sha1
debug2: kex_parse_kexinit: ssh-rsa, ssh-dss
debug2: kex_parse_kexinit_: kex_parse_kexinit_ aes128-cbc, 3des-cbc, blowfish-cbc, accast1 192-acx-cbc: acp cbc: ac debugpit256
3des-cbc, blowfish-cbc, cast128-cbc, arcfour, aes192 -256 -cbc
debug5, hmac-m sha1, umac-64 @ openssh.com, hmac-ripemd160 , hm60-ripemd1 @ openssh.com, hmac -sha1-96, hmac-md5-96
debug2: kex_parse_kexinit: hmac- md5, hmac-sha1, umac-64 @ openssh.com, hmac-ripemd160, hmac-ripemd @ openssh.com, hmac-sha1-96, hmac-md5-96
debug2: kex_parse_kexinit: no, zlib @ openssh. com, zlib
debug2: kex_parse_kexinit: none, zlib @ openssh.com, zlib
debug2: kex_parse_kexinit:
debug2: kex_parse_kexinit:
debug2: kex_parse_kexinit: first_kex_difollow1 group-exchange-sha1, gss-group1-sha1-toWM5Slw5Ew8Mqkay + al2g ==, gss-g ex-sha1-toWM5Slw5Ew8Mqka
debug2: kex_parse_kexinit: aes128-ctr, aes192-ctr, aes256-ctr, aes256-ctr, aes256-ctr cbc, aes256-cbc
debug2: _kexi_pars: zlib, none
debug2: kex_parse_kexinit:
debug2: kex_parse_ brkexinit > debug2: kex_parse_kexinit: first_kex_follows 0
debug2: kse reserved by kexin_parse
> .mdeb1mac server – >> debug2: mac_setup: stumbled upon hmac-md5
debug1: kex: client-> server aes128- cbc hmac-md5 no
debug1: p SH2_MSG_KEX (1024 <1024 <8192) sent
debug1: pending SSH2_MSG_KEX_DH_GEX_GROUP
debug2: dh_gen_key: priv. Critical bits defined: 129/256
debug2: certain bits: 512/1024
debug1: SSH2_MSG_K
debug1: expected SSH2_MSG_KEX_DH_GEX_REPLY
debug3: check_host_in_host / pssh / psknown_host / pssh / psknown_file> : check_host_in_hostfile: match the “debug” array. it is known to match the RSA host key.
debug1: kernel found at /u09/ps/pspro/.ssh/known_hosts: 76
debug2: Specific bits: 481/1024
debug1: ssh_rsa_verify: correct initials
debug2: kex_derive_keys < br> debug2: set_newkeys mode: 1
debug1: SSH2_MSG_NEWKEYS sent
debug1: SSH2_MSG_NEWKEYS expect from debug2: Process set_newkeys: 0
debug1: SMSdeW2acceptSERVICE2 sent: debug service SMSdeW2acceptSERVICE2 receivedSHPT2_MSG_NEWKEYS received from debug1_CEPT_CE2_CEPT_CE2_SERVICE_2_SERVICE_2_Service_service_service2: key: / U09 / ps / pspro / .ssh / id_dsa_1 (40030ef8)
debug2: key: /u09/ps/pspro/.ssh/i d_dsa_2 (40030f78)
debug2: Key: / u09 / ps /pspro/.ssh/ id_dsa_3 (40032338)
debug2: Key: /u09/ps/pspro/.ssh/id_dsa_4 (40032358)
debug1: Authentication that can prodcontinue: publickey
debug3: restart, skip another public keylist
debug3: preferred public key, interactive keyboard, password
debug3: authmethod_lookup publickey
debug3: always preferred: interactive keyboard, password se
debug3: authmethod_is_enabled publickey
debug1: Next public key authentication
debug1: method: No offer keys: /u09/ps/pspro/.ssh/id_dsa_1
debug3: send_pubkey_test
debug2: We submitted your Publickey package, wait for a response
debug1: Authentication that may continue: publickey
debug1: Offer public keys: /u09/ps/pspro/.ssh/id_dsa_2
debu g3: send_pubkey_test
debug2: we have sent an important packet, publickey is waiting for a response
debug1: the server accepts the key: pkalg ssh-dss blen 434
debug2: input_userauth_pk_ok: fp b9: fb: 4f: 35: 24: 4b: 4d: d2: 82: 69 : ba: f3: aa: 64: e 3:58
debug3: sign_and_send_pubkey
debug1: Read from PEM private key succeeded: enter DSA
debug1: Authentication succeeded (public key).
debug2: fd 5 O_NONBLOCK parameter
debug2: 6 fd O_NONBLOCK parameter
debug1: Final hpn_buffer_size = 131072
debug1: Channel 0: Sharp [client session]
debug3: ssh_session2_open: channel_new: 0
debug2: Channel 0: Opens
debug1: Enter an interactive session.
debug2: start callback
debug2: client_session2_setup: id 0
debug1: Dispatch subsystem: sftp
debug2: Sales channel 0: Define request subsystem 1
debug2: fd 4 TCP_NODELAY parameter
debug2: callback completed
debug2: route 0 : open Confirm rwindow 16384 rmax 35000
debug2: tcpwinsz: for 32768 Deny broadcast service: 4
Failed sftp subsystem request for channel 0
Connection closed