Table of Contents
If you have a windows 7 Audit File System, the following article might help you.
Approved
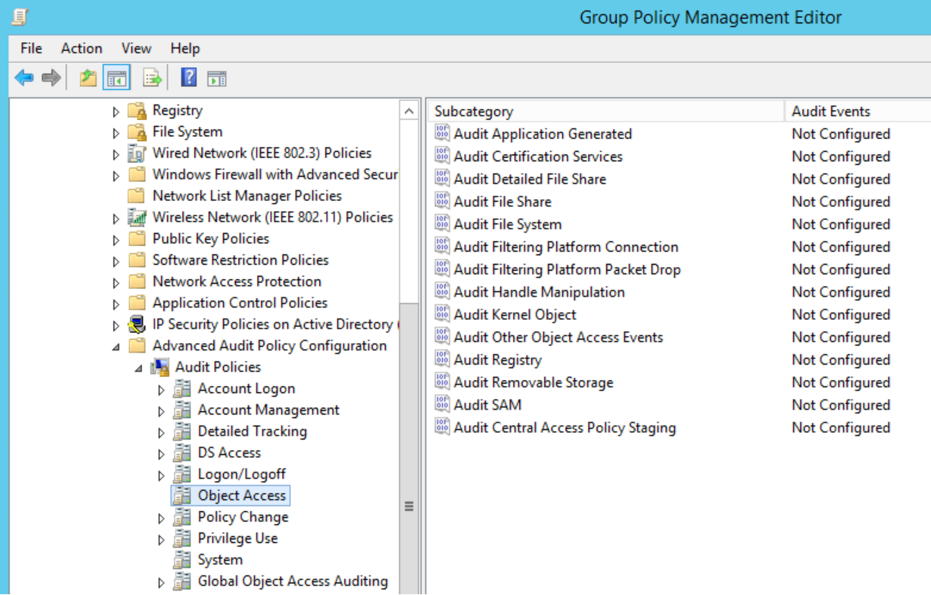
In the 6 windows, select “System and Security” first. On all versions of Windows, open Local Tools and Administration, then Security Policy or Local Security Settings. Some in the Local Security Settings windows, click each arrow or + (plus sign) next to Local Policies, and then enable the audit policy.
File system auditing specifies that it does not matter whether the operating system generates audit functions when users try to access objects in the file system.
in the navigation windows to the file you want to track.Right-click the folder/file with the address and select “Properties”.Security → Advanced.Select the Monitoring tab.Click Add Principal,Select to whom you want to grant permissions for review.In the Audit Entry Package dialog box, select the access types you want to check.
– Track Who Is Actually Reading A File In The Windows Event Viewer
To find out who is reading a document, open the Windows Event Viewer and read “Windows to Logs” . † “Security”. On the right panel there is a “Filter current log” system to receive the relevant events.
Enable Basic Auditing For TheFile And Folder Support
You simply configure audit policies using Group Policy, if necessary Local Security Policy. usage groupA policy for when you want to define monitoring packages for an entire site, domain, organization, or object.The requirement for local security policy settings on a particular workstation or system can be overridden by group policy.
To see who reads the most files, open Event Viewer and Windows and navigate to Windows Logs → Security. In the right pane is the “Filter current to log” option to find matching events. male When either female opens a file, an event with ID fouthy-six is logged. You
Configuring File Access Auditing On Any Type Of Windows File Server
The audit policy can potentially be changed. enabled through group policies obtained from the domain level, through the local security policy in the case of a single file server. For the purposes of this blog post, let’s now enable the Advanced Audit Scheme using Group Policy on a Domain Controller running Windows Server 2016 R2
Protect The Data On Your Windows File Servers With Regular Checks Similar To Access Attempts.
Sometimes users are granted permissions that allow them to read files containing confidentialsocial data that they should not see. For example, an office manager may have unnecessary permissions to read bookkeeping computer files, which could lead to a security breach. In addition, buyers sometimes try to read file types that contain sensitive data that they definitely don’t have access to. Be sure to record attempts to access log files and read these events regularly to keep references to sensitive information under control and thus minimize the risk of information leakage. creating and then deleting files/folders using ADAudit Plus
ADAudit Plus provides comprehensive reports to consolidate all relevant information about files/folders created or deleted in your organization. These reports can be optionally exported, scheduled to be generated automatically at specific times, and added to your inbox. You can also set up alerts to notify you when critical file/folder permissions are misplaced. So you can act immediately.
Approved
The ASR Pro repair tool is the solution for a Windows PC that's running slowly, has registry issues, or is infected with malware. This powerful and easy-to-use tool can quickly diagnose and fix your PC, increasing performance, optimizing memory, and improving security in the process. Don't suffer from a sluggish computer any longer - try ASR Pro today!

Continuous monitoring of activity on your network is one of the latest security best practices because it helps you detect potentially malicious activity early enough to take effect and prevent data leaks, recovery times from the system, and compliance failures. The main methods for monitoring Windows include:
The Windows File System Checker is a very useful tool that allows buyers to track and control whoAccesses files and reads them. The file analysis mark will help you find out exactly what data the attacker was trying to get and steal. In this guide, each of us will show you how to make it easier to monitor the Windows file system and keep track of files.
Right-click a file or file in Windows Explorer. Select Properties. Go to the “Security” tab and just click “Advanced”. Click the Auditing tab, then click Continue. Add users, and sometimes groups, that you want to explore, and select all the checkboxes of the type you want.
Click the Add control, click Object Types. Then check “Computers” and select the computers (file server computers) to which you want to apply the Document Performance Monitor policy settings and click “OK” to apply them. 4. Refresh or refresh the GPO by running any GPUpdate /Force command to apply this scope to all selected file servers. one.